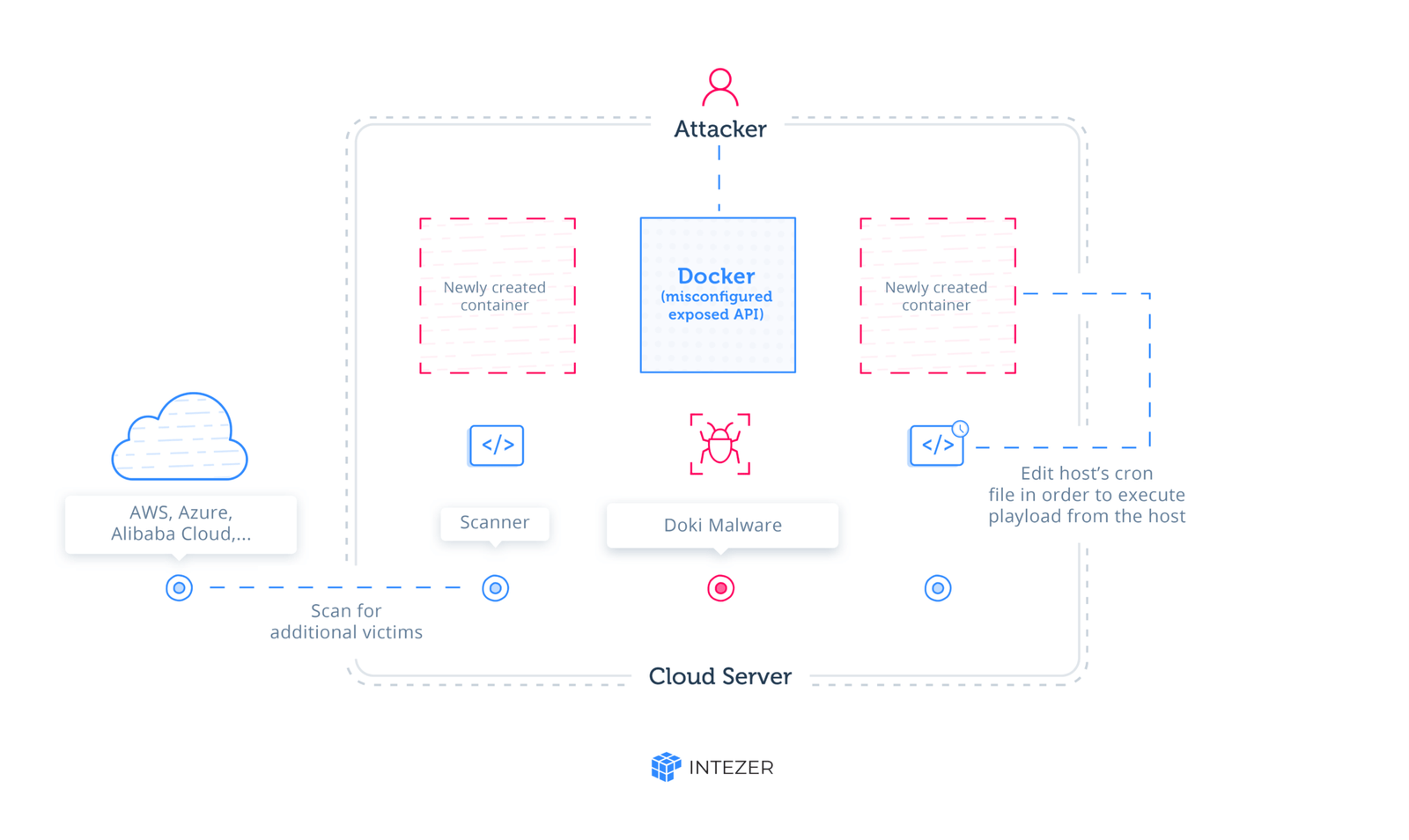
Recently, new malware is traced by researchers targeting cloud services on Linux machines: Doki Malware. The malware is a previously undocumented technique infecting exposed Docker servers in AWS, Azure, and other cloud platforms. The threat landscape for Linux distribution is expanding rapidly. Cyber crooks are advancing in their malicious techniques to knock down systems irrespective of the operating systems. To add to the threat, the increasing shift and reliance on cloud services which are usually Linux based also render such services exposed to prying eyes of attackers.
What is Docker?
Docker is a collection of the platform as a service (PaaS) products. These products are based on virtualisation at the OS level. These products are used to deliver software packages called containers. Containers, on the other hand, are bundles of isolated systems with their own libraries, software and configuration files. They can also communicate with each other well defines channels. The Docker utility on Linux distribution helps in running applications on various locations, i.e. on a private or public cloud.
The Malware
Dubbed as “Doki”, malware is a highly sophisticated backdoor which managed to stay undetected for over six months. The malware was never detected by the 60 malware detection engines since it first appeared on January 14, 2020.
The backdoor is used by attackers to execute codes on the Linux machine. The malware uses a well-formed command-and-control (C2) servers. The malware uses techniques to establish communication with the C2 in real-time. This happens by utilizing the DynDNS service and a unique Domain Generation Algorithm (DGA) based on the Dogecoin cryptocurrency blockchain. The Doki Malware is completely different from the typical crypto miners. What makes it different from other malware variants in the same field is the method it implements to communicate with the attackers by abusing the Dogecoin cryptocurrency blockchain in a unique way in order to dynamically generate its C2 domain address.
The Attack
The threat targets the vulnerability in the misconfigured containers in the cloud environment. To begin with the attack, cyber crooks scan for publicly accessible Docker API and exploit them to create their own containers which are ultimately used to deploy the malware payload.
The container formed is based on an alpine image with curl installed. The image is available on the Docker hub. The image itself is not malicious but rather uses curl commands to perform nefarious activities. And it is observed that as soon as the image is formed, curl commands are executed in the background.
Containers that are created during the attack are configured to bind /tmpXXXXXX directory to the root directory of the hosting server. This leads to an escalation of privileges enabling attackers to access and even modify any file present on the host system with correct user permission.
Abusing Ngrok
Ngrok is a service which provides secure tunnels to establish a connection between local servers and the internet.
The attacker behind the Doki Malware creates unique URLs with by abusing Ngrok. These URLs are of a short lifetime, used to deploy the malware payload using the curl image. The downloaded payload is saved in /tmpXXXXXX directories in the container.
By exploiting the bind configuration the attacker can change the cron utility of the host system. The attackers also use the compromised cron to execute the malware every minute.
The Doki backdoor malware was seen to install two payloads on the host system.
Network Scanner Script
The network scanner uses zmap, zgrap, and jq to scan ports associated with Redis, Docker, SSH, and HTTP.
This malicious script gathers information from the cloud servers and uploads it to another Ngrok URL. This happens when the script acquires IP addresses of cloud servers such as AWS and local cloud providers.
Downloader Script
This malicious script is responsible for downloading and installing various crooked binaries known as crypto miners.
The Doki Malware gives attackers complete control over the configuration of the container, which is created during the compromise of the Ngrok framework, and on the dropped malicious payloads. configuration of the container he creates and the files that are dropped into the container. By using legitimate API commands, the attacker is able to escape from the container he created and execute any code from within the server itself.
Docker Safety
Prefer minimal base images. It is seen that many Docker containers on the Docker Hub are a large number of images that contain many known vulnerabilities.
Least privilege user. The problem with providing root privileges to applications is that such applications on the container broaden the scope of the attack providing attackers with an easy path to compromise the machine and gain escalation of privileges.
This attack is quite a peculiar one and hard to understand. But if you’re someone who is fond of the cloud, beware!