In recent months, hacking e-commerce sites has become a common practice. For a considerable number of years, criminals have been able to steal credit card details from unaware online shoppers without attracting too much attention. People in the security industry were talking about these credit card web skimmers which were doubly sided means both server-side and client-side. Now, Client-side is largely known as Magecart. Some threat authors started to evolve their craft. This has been long since Steganography is used by malware actors to hide malicious data within images that look legitimate and currently, it is being used by cybercriminals to spread credit card skimmers. Hiding malicious code in picture files is a great way to go undetected in the context of website security. In 2014, there was a variant of the Zeus banking Trojan called ZeusVM, which was hiding its configuration data within a picture of a beautiful sunset. The scanners and web crawlers mostly concentrate on HTML and JavaScript files. They often ignore media files. Threat authors are mainly using WebSockets to provide a more covert way to exchange data in comparison to typical HTTP request-responses. Currently, over 5,700 websites have been infected with malware, and with over 100 of those infected with the recently discovered Magecart malware. Some major incidents happened, notably British Airwaysbreaches and the Ticketmaster, to put this growing threat under the spotlight and finally raise awareness among consumers and online merchants. The first publicly-documented steganography-based credit card skimmer took place @AffableKraut was disclosed on 26 December.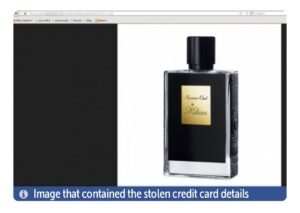
What is Steganography?
Steganography is the practice of concealing information or messages which can be private as well as public, within other non-secret text or data.
The technique of hiding text data inside an image’s source code is known as Steganography. Due to incredible difficulties to introduce text inside an image’s source code without corrupting the actual image file, among hacking groups, the technique is not that common. But hackers are rapidly switching to this technique. A clever security researcher opening the file could easily detect something strange and check the image inside a text editor. Because of this, very few attackers employ these tactics.
What is happening actually?
A new steganography-based credit card skimmer that targets online retail shops has been spotted. This is a report from Malwarebytes Lab. When seen through naked eyes, the image simply looks like a typical free shipping ribbon that is commonly found on shopping sites. However, a deep look at the image reveals JavaScript code has been appended immediately after the end of the file marker. Researchers further mentioned that “All compromised sites were noted using a steganographic skimmer, injected with similar code snippets to load the fake image and parse its JavaScript content via the slice() method.”Similar code snippets were typically after the footer element or Google Tag Manager. For example, an e-commerce website and the various components it loads many of these will be product images, logos and so on.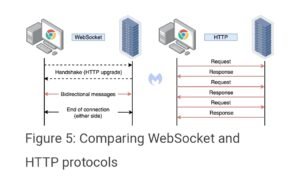
Images resemble any other product photo
The most mindful and interesting fact is that this image was related to products sold on the victim website. Most website owners would not be this nice to come across such images and open it to make sure it worked. At this point, the attacker only had to access this image, then download and extract the data found at the end of the JPG’s source code. If the website owner had inspected the site’s logs for suspicious activity, he would have seen “another” site visitor download “another” image. This happens thousands of times per hour.
An interesting evasion
Researchers found that “The attackers need to load a new WebSocket which can be detected in the DOM(document object model). However, they were sharp enough to obfuscate the code nicely enough that it completely blends in”.  The goal is to hide a connection to a server that is controlled by the criminals over a WebSocket. Such a handshake is enough to steal data. When the malicious JavaScript code runs in the browser, it functions a client handshake request. Once this handshake is established, a series of bidirectional messages are exchanged between the victim’s browser and malicious host. These messages also comprise the credit card skimming code. The only indication that there might be something suspicious is the fact that the file is malformed, with additional data found after the normal end of the file. So after the normal ending of the file, there will be some amiss content. We can look at the image in a hex editor, to better understand what and where this data might be and what are possible changes made. Through some of its strings such as one step checkout or authorize net, we can immediately deduce that this is the credit-card skimming code. During the past years, attackers have significantly shifted their concentration towards online e-commerce platforms, where they found a well fertile ground for collecting payment card data. In most cases, they later sell on underground hacking and carding forums. In comparison to the majority of malware authors that will keep using traditional methods, more advanced actors will come up with new ways to evade detection. Some techniques may only be targeted at researchers, while others may be intended to bypass web crawlers.
The goal is to hide a connection to a server that is controlled by the criminals over a WebSocket. Such a handshake is enough to steal data. When the malicious JavaScript code runs in the browser, it functions a client handshake request. Once this handshake is established, a series of bidirectional messages are exchanged between the victim’s browser and malicious host. These messages also comprise the credit card skimming code. The only indication that there might be something suspicious is the fact that the file is malformed, with additional data found after the normal end of the file. So after the normal ending of the file, there will be some amiss content. We can look at the image in a hex editor, to better understand what and where this data might be and what are possible changes made. Through some of its strings such as one step checkout or authorize net, we can immediately deduce that this is the credit-card skimming code. During the past years, attackers have significantly shifted their concentration towards online e-commerce platforms, where they found a well fertile ground for collecting payment card data. In most cases, they later sell on underground hacking and carding forums. In comparison to the majority of malware authors that will keep using traditional methods, more advanced actors will come up with new ways to evade detection. Some techniques may only be targeted at researchers, while others may be intended to bypass web crawlers.

