We all see Apple as a gold standard for cybersecurity. So it might come as a surprise that more than half a billion iPhone and iPad users are under a risk of a cyber attack. The shocking report came last week from ZecOps, a San Francisco-based mobile security forensics company. The report claims that Apple’s custom-built mail app is vulnerable to cyber-attacks.
How does the attack work?
Hackers were able to initiate the attack by sending a malicious email. This attack that puts iPhone users at risk arguably floods the memory of the device. In some cases, email without a body content was also able to trigger the vulnerability. The malicious email crashed the app and forced it to reboot. The reboot allows the hacker to get access to steal data on the device such as images and contacts stored on the phone. This vulnerability is limited only to iOS (iPads and iPhones) so the Mac users can have a breath of relief.
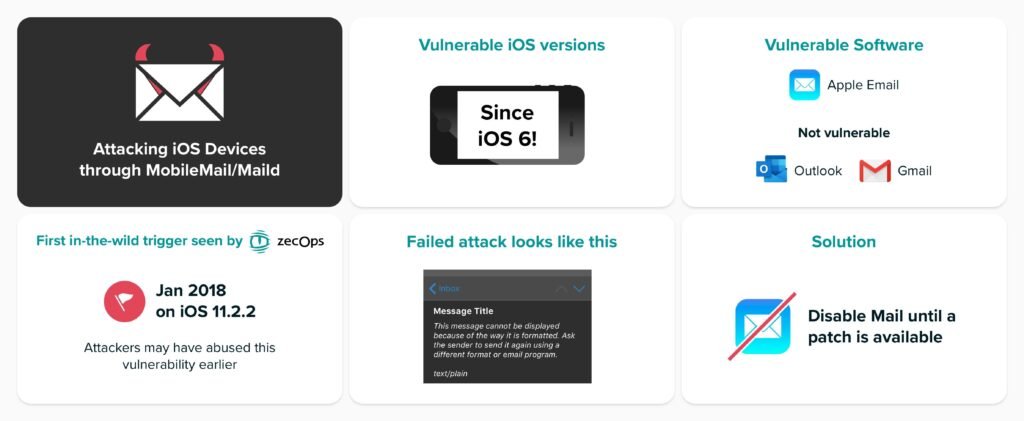
Are you safe?
Going by the report, every iOS version since iOS 6 is vulnerable to this exploit. Even the latest and newest iOS 13 shares the same vulnerability. The vulnerability existed since 2018. The attackers have most probably used these vulnerabilities in the past as well. One good news out of this report suggests that third-party email apps are not under any such danger. Apps like google and outlook can still be used without any restrictions.
Were you attacked?
There are chances the attackers might also have tried to attack you. After any such attack, the mail app crashes. It also results in a temporary slowdown of this mobile application. A handful of unsuccessful attacks were also spotted by ZechOps. The attack gives the attacker the right to delete the email which was used for infiltrating the device. This essentially clears any backtracking possibility. In case of the failed attack, the victim will receive an email showing the message; “This message has no content”. Live pictures of the same are attached below
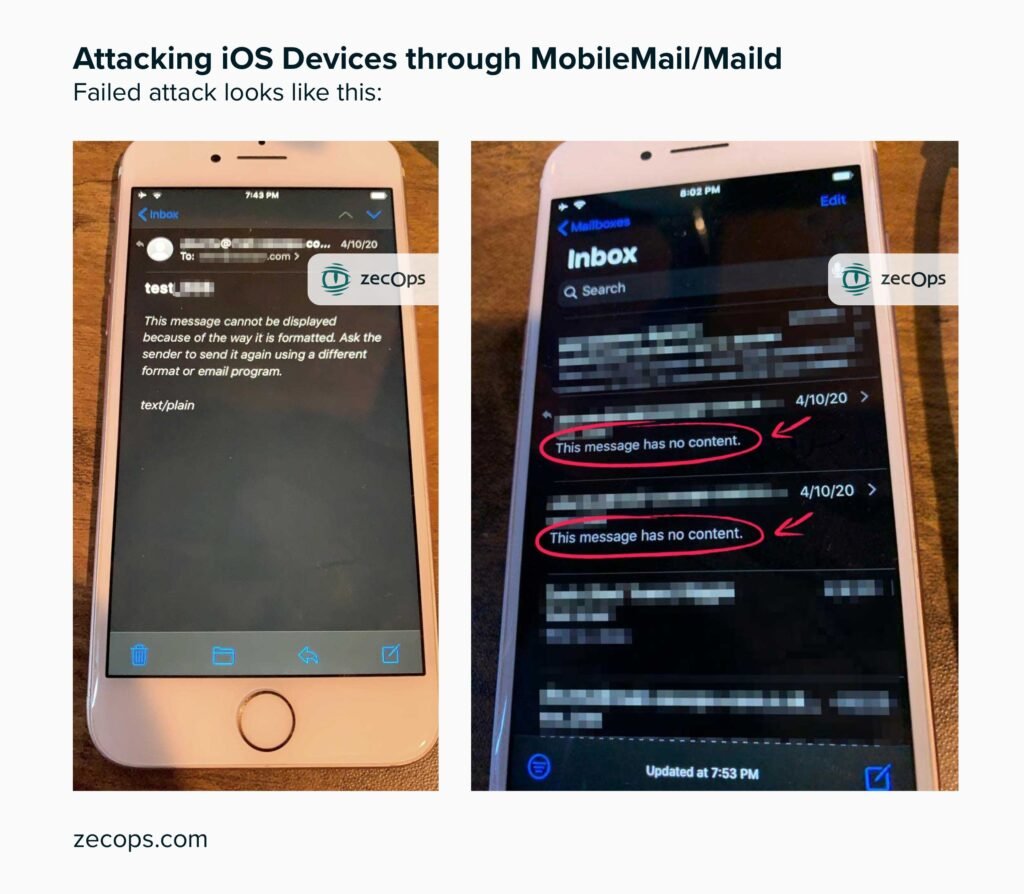
The Discovery
Investigating a sophisticated cyberattack attack in 2019 Zechops chief executive, Mr. Zuk Avraham came to know about this attack. He was able to identify more about this vulnerability based on data from “crash reports”. He claims that this attack is a part of a series of attacks that are being used. All these attacks when combined can give full remote access to hackers. Identifying one attack of this chain may serve as a serious blow to the attackers. But their identity is still unknown. Based on the data from crash reports he was also able to replicate the controlled crashes and study them in detail.
The Known victims
As per the current know information, the attackers have tried to attack only high profile users. Zechops also released a small list of suspected targets.
- Individuals from a Fortune 500 organization in North America
- An executive from a carrier in Japan
- A VIP from Germany
- MSSPs from Saudi Arabia and Israel
- A Journalist in Europe
- Suspected: An executive from a Swiss enterprise
The list gives a clear indication that the attacks were carried out for victims around the globe. If the attack is limited to a specific area, identifying the perpetrator becomes easier.
Sudden Insurgency
With the majority of people working from their homes via their pc, the cybercrime rate is also rising. The number of cyberattacks has shot up especially in those apps which are helping people to work from home. Zoom is facing its biggest vulnerability issue ever. Google is also facing the occurrence of repeated security loops holes in their web browser and chrome. Recently Google removed several chrome extensions from the web store and 100+ android apps from the play store. Hackers are also using coronavirus news to spread false information via emails. With all this crime happening around the world, the news of iPhone users at risk should not be a complete shocker.
How to secure yourself?
One of the apple’s spokesperson has acknowledged a flaw in their software. Apple has already these vulnerabilities in its latest beta. Until a patch is available, it is advisable to disable the mailing app. Also, it is advisable not to open emails which raises suspicion. Always keep looking for clues like broken English, misspelled words, unusual fonts, or unknown email addresses. All these clues are usually present in fraud and malicious emails.

