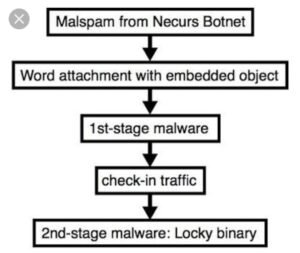
A cybercrime botnet operation that, within about five years of its existence, has been named one of the largest botnets in the world, is the Necurs botnet. The Necurs botnet is a wide distributor of many pieces of malware, most notably Locky. The bottom report is that Necurs is indirectly responsible for a major chunk of cybercrime. According to recent reports, cybercrime damages are expected to cost the world $6 trillion by 2021. This magnitude alone makes it worthwhile to get to know more about one of the top players in that dangerous game. Necurs emerged in the year 2012 as an infector and rootkit and quickly partnered with elite cybercrime gangs to become part of the top spamming and infection forces in the malware chain. When compared with other most popular botnets, Necurs stands out due to its technical complexity, partnership diversity and continued evolution in an era when even the most complex malicious infrastructures can no longer withstand disruption. In the last year alone, we have seen Necurs take on various roles. After being Linked with the spam distribution of the Dridex gang, it is used to spread one of the world’s most nefarious banking Trojans. It has also moved to mass distributing Locky, Dridex’s ransomware child, then added distributed denial-of-service (DDoS) attacks. Most recently, Necurs moved to pump-and-dump stock scam distribution before returning to spreading millions of Dridex-laden spam emails in a single day.
Distributed malware are as follows
- Bart
- Dridex
- Locky
- RockLoader
- Globeimposter
The Necurs Botnet: A complex Box of Malicious Spam
In 2012: Necurs Launches With a Bang
The Necurs botnet emerged in the dying months of 2012 and launched with a bang when it was reportedly detected in over 83,000 infections on endpoints all over the world. Necurs never had a calm beginning. Upon its early emergence, Necurs’ operators started using a Dot-Bit domain to create a peer-to-peer network that would allow them to evade detection in quite an interesting manner. The bit TLD top-level-domain was created outside the domain name system, which means it is not controlled by the Internet Corporation for Assigned Names and Numbers (ICANN). This domain resulted in a decentralized Domain Name Server (DNS) in which the TLD is not owned by any single entity and DNS lookup tables are shared only on a peer-to-peer basis. This shows that DNS servers can be neither updated nor seized by any authority, and once a domain is registered, only its owner can control it.
In the year 2013: Game-Not-Over Zeus
By the year 2013, Necurs went into second gear and started leveraging the Upatre loader to make way for itself and delivering the Gameover Zeus malware to compromised endpoints. It is a well-known fact that Gameover Zeus was a malware variant developed and controlled by none other than Zeus’ original developer and his cybercrime gang. This suggests that the Necurs operators were linked to the very centrum of the banking malware elite. Malicious emails or malvertising campaigns carrying Upatre would download Gameover Zeus into a compromised PC in 2014. This time, Gameover Zeus was the one who runs Necurs. The addition of Necurs’ rootkit features made it nearly impossible to remove Gameover Zeus from the infected PC.
2014 – 2015:The Ransomware Era
CryptoLocker was one of the most infamous ransomware codes at that time, and a cybercrime business that reaped an estimated $30 million in illicit profits within a mere time i.e.100 days.
In 2016: The Dridex-Locky Gang Era
By the mid of 2016, Necurs turned a new page in its operations. It started using its million-strong botnet as a spamming infrastructure and also launched a partnership, by no means lesser than its previous one, with the Dridex malware gang.
Dridex is a sophisticated modular banking Trojan project based on the original Bugat Trojan’s source code. Dridex first evolved in June 2014 and rapidly emerged into one of the top malware threats in the financial sector. It targeted banks in over 30 countries across the globe, focusing on businesses and robbing its victims of millions of dollars in each attack. This time, Necurs made the rounds, serving itself with a side of DDoS module that was added to it back on September 16. For size, of over 1 million active bots at any given time, a DDoS attack leveraging the Necurs botnet could far exceed the volume and effect of attacks the size of recent Mirai botnetonslaughts.
In March 2017: Pump-and-Dump Stock Scams
Next, Necurs diversified its portfolio, and in March 2017, it swamped masses of email boxes with pump-and-dump stock scams — quite a peculiar choice considering its malware-ridden past. IBM X-Force researchers saw a sharp rise in Necurs spam on March 20, 2017. At this point, the botnet was sending at least seven different versions of an email crafted to entice investors to buy shares of a little-known media holding company in the U.S. This new trend for Necurs was somewhat highly surprising since penny stock scams are considered rather outdated. Yet it appeared that Necurs succeeded in pumping its unwitting target’s stock value, which may have enabled its operator to reap the illicit rewards. It likely worked well enough, because Necurs was right back at it a week later with yet another set target. Now, a small firm that develops marketing channels to distribute third-party fitness equipment to wholesale markets in the U.S. was the subject of Necurs’ affection. Necurs’ botnet succeeded once’s again, pumping the stock price high enough to yield a profit to those who stand behind it.
In April 2017: Dridex Spam Skyrockets
Dridex’s developers were quite hard at work during the first quarter of 2017, tweaking the malware’s capabilities. But they also got ready for a major version release.
What Makes Necurs this much Resilient?
Let’s go through the factors that contribute to its strength.
Kernel Mode-RootKit
The most significant highlight about Necurs is that, unlike common botnet malware such as Kelihos, Necurs has kernel-mode rootkit capabilities. It is composed of two, a kernel-mode driver and a user-mode component. Kernel-mode rootkits are malicious applications that run in the kernel of the OS with complete rights to system resources, including both software and hardware, which grants them the deepest privilege level, right in Ring 0.
Programming kernel-mode rootkits are considered an advanced skill, and any error in code can cause the kernel to crash, thus deteriorating the entire operating system.
ModularArchitecture
Another significant feature of Necurs is its modular architecture. The typical botnet malware spread spam or download other malware is relatively simple in technical terms. This is not the case with Necurs.
Necurs’ modularity is notable that allows it to switch things up when its operators choose to change its vocation, partner with other malware distributors, use it for pure spam, or leverage its hold on infected endpoints to deliver malware or be delivered as such.

Anti-AV Features
Necurs manages to infect a large number of endpoints when judged by its spam volume capacity. It is believed to control between 5 and 6 million zombie bots, of which at least 1 million are active at any given time period. Indeed, A sizeable operation
DGA Double-Edged algorithms:
Domain generation algorithms (DGA) are seen in various families of malware that are used to generate a large number of domain names periodically, to be used as rendezvous points with their C&C servers. Without breaking the algorithm that regulates them, each domain name is unpredictable and made up of incoherent sets of letters. These domains are therefore impossible to use to identify malware families when examined individually.
DGA No. 1 is used with detecting lab environments to prevent Necurs from running in a sandbox. At a time, this DGA only generates four domains.
Hardcoded set, which is a predetermined list of domains, may be used as a fallback to call the C&C server. This phase cycles between 16 different domains. If there is only one domain on the given list, Necurs will repeat it 16 times.
DGA No. 2 is targeted with generating 2,048 domain names, covering over 43 different TLDs. These die out every four days. Such a feature is quite rare for botnet malware, and even sophisticated banking Trojans use only one DGA layer. This makes Necurs more resilient to potential interception and much harder to take down overall.
Mitigating Advanced Threats
The Necurs botnet carries powerful malware, but still, it can never be a match for good browsing and computer hygiene practices.

