Ransomware is the new normal for enterprises and businesses in 2020. Through advanced tactics and well-crafted custom malware, hackers compromise host system, steal sensitive information and demand ransom to restore data. Recently researchers at Proofpoint tracked a Hakbit ransomware campaign which is targeting organizations in Austria, Switzerland and Germany. Moreover, this campaign uses malicious MS-Excel attachments to infect systems.
Hakbit ransomware campaign became operational in 2019, taking victims in the US and Europe region. This low-level campaign targets mid-level employees belonging to healthcare, pharmaceutical, financial, legal, business service, and retail sectors. Besides, Hakbit is developed on Thanos ransomware builder.
Furthermore, the campaign uses GuLoader dropper and malicious MS-Excel attachments to spread the ransomware by launching spear-phishing emails through GMX email provider. Ransomware encrypts host system’s files and data and presents a ransom note mentioning the ransom amount to restore system files. Likewise, Hakbit executes its attack by injecting a malicious macro. After encrypting the files the operators demand a ransom of 250 Euros in Bitcoin.
Hakbit Campaign Tactics
The ransomware attacks are more or less remain the same in their methodologies.
Hakbit ransomware campaign launches spear-phishing emails to infect MS-Excel on the victim system. These emails contain financial lures, such as “Fwd: Steuerrückzahlung” (Translated: Tax Repayment) and “Ihre Rechnung” (Translated: Your Bill). The emails are delivered via GMX, a free email provider that primarily serves a German-speaking European client base.
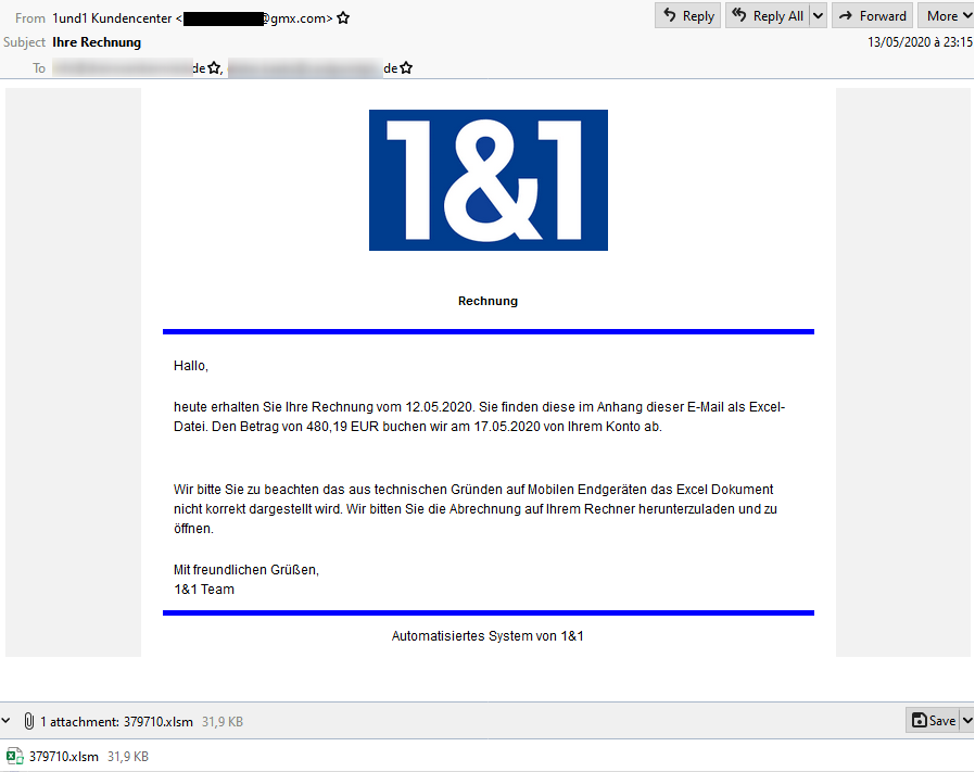
These low-volume spear-phishing campaigns, also called as snowshoes spam attacks, use multiple domains to send relatively small blasts of bogus emails to circumvent reputation- or volume-based spam filtering. The large volume spams were deployed in information technology, manufacturing, insurance and technology giants. The Hakbit campaign seeks for firms which reveal individuals’ business contact details on company websites and/or advertisements. And accordingly chooses its targets.
The impersonating MS-Excel attachments once opened by the user prompts them to enable macros. Since macros are not operated on mobile devices, threat actors direct the recipients to open attachments on their computer. The attachments leverage malicious macros to download the GuLoader, which executes and downloads the Hakbit ransomware.

GuLoader
It is a popular Visual Basic 6 (VB6) downloader that abuses cloud services. Researchers at Proofpoint found the downloader in the wild, which is now one of the most dangerous malware droppers.
This portable executable (PE) decrypts shellcode containing the major functionality. Initially, GuLoader was used to deploy Parallel RAT, but soon got employed into other info-stealers. This VB6 downloader stores its encrypted payloads on cloud services like Google Drive and Microsoft One Drive. GuLoader is often observed embedded in .rar or .iso files. The dropper is used to download remote access trojans (RAT) on infected systems, just like in Hakbit campaign.
An Italian company was allegedly selling GuLoader as legitimate encryption software. But it was used for second-stage malware injection, instead.
In this campaign, the PE downloads and executes Hakbit ransomware. This ransomware is believed to link with the Thanos ransomware, as both resemble in code structure, string reuse, the ransomware extension and the format of the ransom note.
After injection and compromising the victim’s system, Hakbit encrypts files using AES-256 encryption present on the system. HakbitIn addition to it, the malware deploys a ransom note demanding 250 Euros in Bitcoins to unlock and restore files.

Hakbit exemplifies as ransomware which preys on specific targets. Because of delivering emails using GMX, the threat actors use multiple IDs, which makes it difficult for experts to track them.
How to be safe?
56% of organisations reported being a victim of ransomware in 2018. This number increased to 62% in 2020, according to a recent report from CyberEdge.
Ransomware attacks are advancing exponentially in their techniques, ever since the first ransomware occurred in 1989, targeting a healthcare industry (Latest ransomware attack of 2020: DoppelPaymer ransomware). These attacks pose various threats ranging from privacy breach to public humiliation. And this rampant practice asks for immediate and efficient safety measures.
Backup your system files, locally and in the cloud
Firstly, backing up your files and sensitive information will prevent any cyber crook to gain access to it. And secondly, if you fall prey to any cybercriminals activity (Hakbit for instance), you may not have to pay the ming boggling ransom to restore your files.
Network Segmentation
Microsoft suggests organisations to segments their networks, with each segment requiring a different credential. This prevents complete system compromise in a single attack.
Install Anti Malware / Ransomware Software
It is often seen that the latest of the antivirus utilities fail to combat the latest ransomware attacks. Therefore, it is important to be equipped with antivirus, anti-malware, and anti-ransomware protection software.
And it’s crucial to keep the virus definitions up to date.
Companies and employees fall victims to ransomware attacks because of lack of training and awareness about countering the latest and rampant cyber treats in practice. Employees should recognize the signs of spear-phishing emails. This is possible when they are always updated regarding the cybercrimes and their mitigation methods.


