Recently, Nvidia, the market leader in the design of graphics processing units (GPUs), warns Windows gamers about the reported flaws in the GPU drivers. These high-severity vulnerabilities can be exploited by attackers to steal sensitive information, gain privileges and launch DoS(denial of service) attacks on the affected Windows gaming devices. Nvidia has also officially declared about the flaws along with their mitigations.
Nvidia (NVIDIA or nVIDIA) is an American multinational company which designs graphics processing units (GPU) for gaming enthusiasts. The software component enables high-level, gaming-optimised performance for high-end applications to run efficiently, giving a mind-boggling experience to gamers.
Several security experts reported the severe vulnerabilities in the Nvidia drivers. Nvidia analysed the flaws which can jeopardize systems’ security and accordingly issued guidelines and mitigations about the vulnerabilities.
Flaws in NVIDIA Display Driver
Out of the reported vulnerabilities, two were categorised as high-severity flaws. NVIDIA GPU Display Driver contains a vulnerability-CVE-2020-5962-in the NVIDIA Control Panel component, which provides access to the GPU driver settings. This serious flaw can also let attackers gain control of other utilities present on the system, corrupt system files which may lead to DoS and escalation of privileges.
The other severe fault-CVE‑2020‑5963-is present in the Inter-Process Communications APIs in the NVIDIA CUDA Driver, a computing platform and programming module developed by NVIDIA. This vulnerability springs from improper access which can lead to code execution and further can be leveraged for denial-of-service or information disclosure.
Furthermore, the GPU display driver also contains four medium-severity faults.
-
CVE‑2020‑5964: This vulnerability is present in the service host component of the driver posing a threat to applications resources integrity. This can allow cyber crooks to execute DoS, code execution and information disclosure.
-
CVE‑2020‑5965: Present in the DirectX 11 user mode driver (nvwgf2um/x.dll).
-
CVE‑2020‑5966: Contained in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape, in which a NULL pointer is dereferenced, leading to potential attacks.
-
CVE‑2020‑5967: Present in the UVM driver.
All these four medium-severity vulnerabilities can lead to denial-of-service, code execution and information disclosure.
Flaws in NVIDIA VGPU
Nvidia’s Virtual GPU Manager is a tool that enables virtual machines to interact directly with a single physical GPU present on the system.
Nvidia also mentioned four high-severity flaws rendering the system and the drivers in serious risk. All four vulnerabilities are present in the vGPU Plugin.
-
CVE‑2020‑5967: This vulnerability does not restrict (or incorrectly restricts) operations in the boundary within the boundaries of the resource which is accessed by an index or pointer, such as memory or files.
-
CVE‑2020‑5969: This fault present in the vGPU plugin validates a shared resource before using it, causing a race condition leading to DoS, code execution or information disclosure.
-
CVE‑2020‑5970: The nature of the flaw is the same as that of CVE-2020-5969. In addition to Dos, it allows attackers to tamper with the system’s security.
-
CVE‑2020‑5971: In this, the software reads from a buffer by using buffer access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer, which may lead to code execution, denial of service, escalation of privileges, or information disclosure.

NVIDIA versions
All these reported Nvidia flaws are witnessed in the GeForce, NVS, Quadro and Tesla software products which are operated on Windows. Nvidia warned the users about the faults it has stomped. Earlier in March, the company fixed several high-severity present in the display driver, letting attackers launch DoS or code execution attacks. Last year, a slew of patches were issued which affected two popular gaming products.
Mitigation
Nvidia recommends consulting a security or IT professional to evaluate your specific configuration. It has also issued the updated versions with rectified faults for Windows and Linux OS.
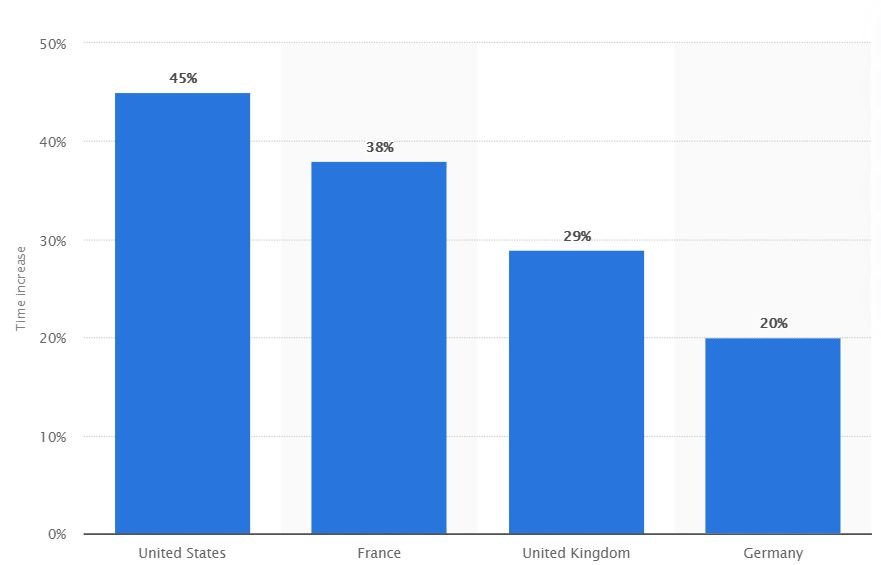
Amid this critical time, where we all are stranded at our homes, gaming is a way out from the stress. According to statista, there’s an increase in video gaming worldwide. And Nvidia being the market leader in designing GPUs and SOCs, these exposed vulnerabilities can give cyber crooks a chance to exploit numerous systems.
Just like antivirus software needs an update for new virus definitions, many utilities require such updates. Each update is focused to mitigate a particular problem. So it is always beneficial to keep the software and drivers available on the system up to date. This prevents any vulnerability which was previously present from being exploited and also updates come with more services and upgraded quality.
Be safe, Be updated.


