An advanced persistent threat (APT) group managed to produce post-compromise tools to takeover Microsoft Outlook in the targeted system. Researchers from the security firm ESET, states in a new report that the Gamaredon hacking group are deploying new sets of malicious tools to send spear-phishing emails to victims’ contact lists.
Gamaredon(aka Primitive Bear) is a notorious Russian-based APT group, allegedly known to have links with the Russian government. Since its inception, Gamaredon has targeted various organisations. The group has targeted the Ukraine government and its military forces frequently to acquire sensitive and intelligence information. What makes Gamaredon unusual is that with intensified exploitation and intelligence gathering of organisations, the group rarely bothers to disguise its presence. Though the group has advanced tools with the capability to remain as stealthier as possible, its primary focus has been to penetrate deeper into the target’s network while exfiltrating data.
Recently, researchers from the security firm ESET, reported that Gamaredon hackers have added new tools to their arsenal. A custom Visual Basic for Applications-VBA-project file, along with an OTM file(Outlook VBA Project) is used to compromise Microsoft Outlook. Henceforth, the macro script disrupts the security settings and send spear-phishing emails with malicious attachments to the whole contact list or a defined sample. This new malicious macro injected in the target system can further tamper with the system security by forcing downloads of malware variants the targeted system.
How does the attack work?

The attack begins when the system is compromised with a phishing email containing a malicious module, called the CodeBuilder module, gains access to the system via a phishing email with an infected Word or Excel attachment. This malicious CodeBuilder module has a custom VBA macro file embedded in it.
After the system is compromised, the CodeBuilder module triggers the VBA macro script to kill the Microsoft Outlook process and disarm the security tools, by altering the registry values.
The malicious script then injects an OTM file in the VBA project file of Outlook. This allows the attackers to gain access to the victim’s contact list in Outlook.
After this, the malicious scripts start producing spear-phishing emails, that can target people in the contact list. The VBA macro can also build new malicious documents that can be attached to the newly generated phishing emails.
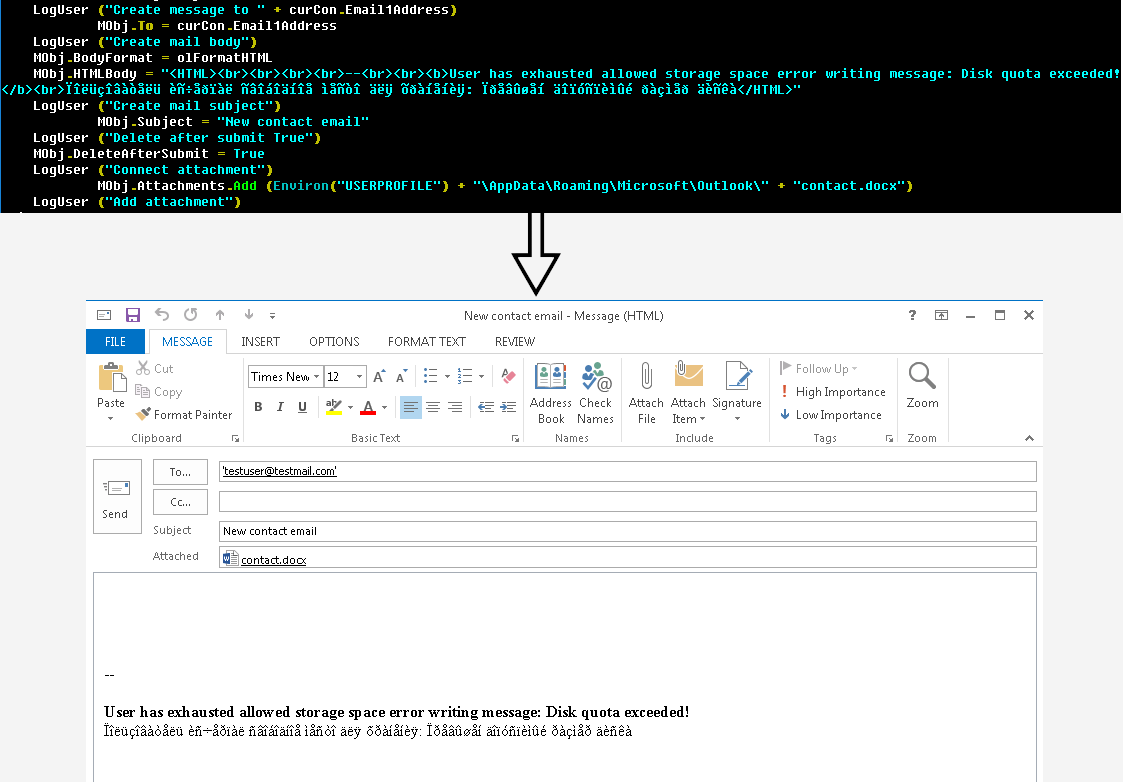
After disarming the security tools and producing spear-phishing emails, the script relaunches Outlook with a special option, /altvba <OTM filename>, to send emails to the people in the contact list.
Hackers then send the produced malicious emails using the victim’s account to people in the contact list.
It’s new and creative!
This new notorious advent of Gamaredon is undoubtedly a serious threat to thousands of users around the world. However, experts have found it unique and creative in various ways.
Hacking groups/individuals frequently use email accounts by compromising systems to send malicious emails. But ESET experts found that the way Gamaredon members employed Outlook macro and OTM file to send spear-phishing emails to potential targets, is something they have not seen before.
The ESET report also states that Gamaredon hackers sent emails to:
-
Every contact in the victim’s contact list,
-
Every contact within the same organisation, or
-
A predefined list of targets.
This method is efficient as documents are often shared between the members of a particular organisation. As phishing emails are sent from a familiar email address, it increases the likelihood that the target recipients will open them. It provides the Gamaredon group to penetrate deeper into an organisation. This way, Gamaredon maintains persistence within an organisation it is targeting, enabling them to move laterally within the compromised network.
Along with maintaining persistence, this attack allows the group to plant backdoors and forcing download other malware to gather sensitive information.
Stay Safe
Analysing and studying this new arsenal of Gamaredon, analysts and experts have found bugs in the Gamaredon CodeBuilder module coding. This indicates that hackers are still refining their new tactics.
- Experts say that a way to prevent these types of attacks is to run executables and raise awareness amongst employees, about how a system can be compromised with phishing.
- Avoid clicking links in emails. Hover the cursor over the link to verify that the URL matches with the anchor’s text and email’s stated destination.
- Limit sharing personal details like contact number, email address on social media and other websites as hackers get hold of personal contact details through websites.
- Updating security settings to secure system macros in Office documents and reviewing logs for any system intrusions should be implemented to prevent spear-phishing carried attacks.
- Another popular method for threat detection is to leverage SIEM signatures and perform endpoint scans for malicious payloads.
Keep yourself updated related the newly introduced safety measures against cyber threats. And report when you find any suspicious email.


