Ransomware-a familiar adversary for enterprises and individuals operating online, wholly. The practice of accessing systems, evading detection, keeping data as a hostage and coercing victims into paying ransoms is what a ransomware attacker has expertise in. Ransomware attacks are advancing exponentially in their techniques, ever since the first ransomware occurred in 1989, targeting a healthcare industry. A familiar name in the world of notorious ransomware gangs is the DoppelPaymer Group. What makes it more prevalent is the threats it has posed not much time before.
The ransomware attacks more or less are similar in their approach. The responsible group first mentions the company’s name it has targeted on its “official” website. And then publish some of the “stolen” data as “proof”. Just like a pinky finger on the doorway in case of kidnapping. After the asked ransom is paid (usually in BitCoins), the group removes the name promises to delete the stolen data, which is unlikely. If the company fails or denies to pay the ransom, the threat actors delete the data from the company’s server and dump the stolen data on dark-net to meet their attack costs.
“We have been stealing data for the past year and occasionally selling it anonymously to help cover our gang’s costs”, says DoppelPaymer group to Bleeping Computer.
About DoppelPaymer
The ransomware family, DoppelPaymer, has become under the lens of security experts and firms after invading renowned enterprises in 2020.
DoppelPaymer group encrypts data and coerces users to pay ransoms to restore and decrypt the files. The malware’s builds were identified back in April 2019, but the initial victims were seen in June 2019.
DoppelPaymer group got its name by the researchers who tracked the ransomware attacks by the group. And the threat actor behind the ransomware attacks had also adopted the same name.
The DoppelPaymer ransomware’s code resembles BitPaymer ransomware operated by INDRIK SPIDER. Researchers suspect that some individuals have split from the latter and employed the segments of Dridex and BitPaymer to conspire their own big game through The DoppelPaymer Ransomware. Both ransomware versions of INDRIK SPIDER share most of their code with DoppelPaymer malware.
INDRIK SPIDER, the predecessor of DoppelPlaymer group is a family of cybercriminals formed in 2014. They internally referred to themselves as “The Business Club”. Since their inception, INDRIK SPIDER developed their own custom malware called Dridex and BitPaymer. Dridex was primitive, but with time it became sophisticated and professional. In 2017, the group introduced BitPaymer ransomware which uses TOR-based payment portal for ransom demands. All this by implementing crypto-locking.
DoppelPaymer Methodology
BitPaymer and DoppelPaymer ransomware resemble each other in their approach and methodology. Even, the ransom notes of the two are the same, except the threat actor has replaced “BitPaymer” with “DoppelPaymer”.
The technological traits used by DoppelPaymer includes:
-
Encryption Method: 2048-bit RSA + 256-bit AES2048-bit RSA + 256-bit AES.
-
Encrypted files renamed with “.locked” extension. Latest variants of the ransomware have “.doopeled” extension.
-
ProcessHacker Technique: tampering with the services interfering with the encryption process.
DoppelPaymer ransomware access the system usually through Dridex Trojan. But the distribution of the ransomware is not limited to a single practice. There are various methods used to inject the ransomware observed over the year:
-
Insecure RDP configuration
-
Email spam and malicious attachments
-
Deceptive downloads
-
Botnets
-
Exploits
-
Malicious advertisement
-
Web injects
-
Fake updates
-
Repackaged
-
Infected installers
After injecting the DoppelPaymer ransomware, the attack will begin by encrypting the files (video), along with the creation of a readme text file with the name “howtodecrypt.txt”. This text file contains the ransom notes, containing further steps for the victim to follow.
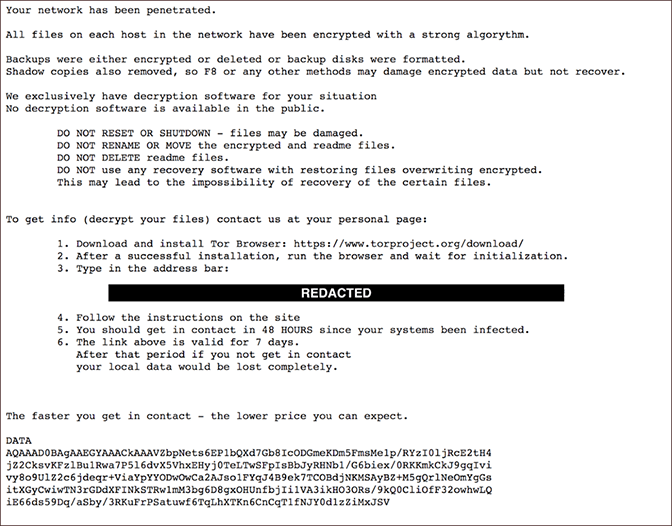
Unlike BitPaymer ransom note, the victim will not find the ransom amount mentioned in the ransom note of DoppelPaymer. Instead, the victim is directed to the payment portal through a TOR-based URL.
After accessing the payment portal the victim will be provided with information such as a unique reference ID to identify the victim, a countdown timer and the BTC wallet address for BitCoin transfer.

Just like the other ransomware groups, such as MAZE, DoppelPaymer has also released its official site to publish stolen data and the victim’s name.
Recent Attacks
DoppelPaymer has targeted many enterprises over the year.
-
In June 2020, the operators of the DoppelPaymer ransomware infected the network of Digital Management Inc. (DMI), one of NASA’s IT contractors.
-
In April 2020, DoppelPaymer Ransomware targeted the City of Torrance of Los Angeles and leaked approximately 200+ GB of the stolen files.
-
In the same month, the DoppelPaymer crew leaked details of Boeing, Lockheed Martin, SpaceX, and Tesla after the contractor Visser Precision refused to pay the ransom
Safety Measures
-
According to Microsoft, to prevent ransomware attacks, the organisations should implement network segmentation, use strong credentials, and assign the least permissions to employees.
-
Experts say installing an EDR (Endpoint Detection and Response) service can counter such attacks.
-
Always keep backup of sensitive and critical data.
-
DoppelPaymer and other such groups use spams, botnets and deceptive downloads to penetrate organisations. Refrain from download suspected or unknown attachments in emails.
Keeping yourself and employees of your organisations updated about cyberattacks will improve cyber awareness and chances of similar cyberattacks.


