Recently, in the virtual meeting of Black Hat USA 2020, researchers have found a unique, queer yet effective way to hijack the android devices through a new Bluetooth vulnerability called BlueRepli. This enables attackers to gain access to the device without any interaction with the victim, stealing private information of the user.
An Overview
Bluetooth technology uses short-wavelength radio waves to transfer data between devices like mobile devices, IoT devices, printers, speakers, headphones and the list goes on.
There have been numerous instances of cyber crooks tampering with the Bluetooth protocols to compromise devices to perform their nefarious activities. With attacks like BlueBorne, KNOB, or BadBlueTooth, cybercriminals have appended their list of exploiting Bluetooth devices with another attack called BlueRepli. Researchers said that only Android devices are vulnerable to this attack. iPhone devices are safe!
The range of devices running the Android operating system is huge. Having a large attack landscape with tens of millions of users in the world, attackers are focusing on exploiting Android devices to spread their reign through other Android devices.
This leaves Android devices always vulnerable to cyberattacks; what bothers android users is that Google’s delay in releasing patches for vulnerabilities!
BlueRepli Vulnerability
Security researchers Xin Xin and Sourcell Xu from California-based cybersecurity firm DBAPPSecurity disclosed yet another Bluetooth vulnerability: BlueRepli.
Using this vulnerability, attackers can bypass the Bluetooth authentication on Android devices without detection or interaction with the victims. Attackers can steal sensitive data from the host device like call records, contacts, and SMS verification codes. Furthermore, hackers can send fake SMS to the victim’s contact list.
Threat actors can bypass the Bluetooth authentication by impersonating a previously connected device. Therefore, not requiring any permission from the victim. Another way to hijack the devices is through disguising as a trusted application asking permission to share data, just like in the case of a vehicle’s infotainment system.
In the core, BlueRepli is an abuse of the Bluetooth Profiles. Bluetooth profiles enable connectivity between various application scenarios. They are a set of rules to govern about connectivity including sharing data between devices. For example, there is the Phone Book Access Profile (PBAP) to enable access to a user’s phone book, while the Message Access Profile (MAP) provides access to text messages.
Researchers also noticed that this vulnerability doesn’t work with iOS devices. Moreover, this zero-day vulnerability is due to the negligence of a mobile vendor company which has over 100 million Android devices working around the world.
Surprisingly, the researchers notified Google and Android Open Source Project (AOSP) about the Bluetooth vulnerability, but the issue is still there.
BlueRepli Working
The attackers gain access to Android devices primarily through two techniques:
-
The most common is through the familiar dialogue box which appears when a device requests to send or receive data. A yes/no dialogue box to accepts the connection or a six-digit number is presented to secure connection.
-
‘Just Works’ Attack: With this technique, the attackers needs no interaction with the victim to penetrate the device. This Bluetooth technique called the ‘just works,’ can bypass the need for user interaction to establish a connection, getting escalation of privileges. This attack can happen with several other methods.
The first is a deception-based attack where the attacker may secure a connection through pretending to be a Bluetooth device or a trusted application like Skype (just say). The attacker first gets the target device’s Bluetooth address by simple scanning. Then, by impersonating, the attackers request to gain access to phonebook or SMS. After gaining these privileges, the attackers can exfiltrate sensitive information without the victim’s knowledge.
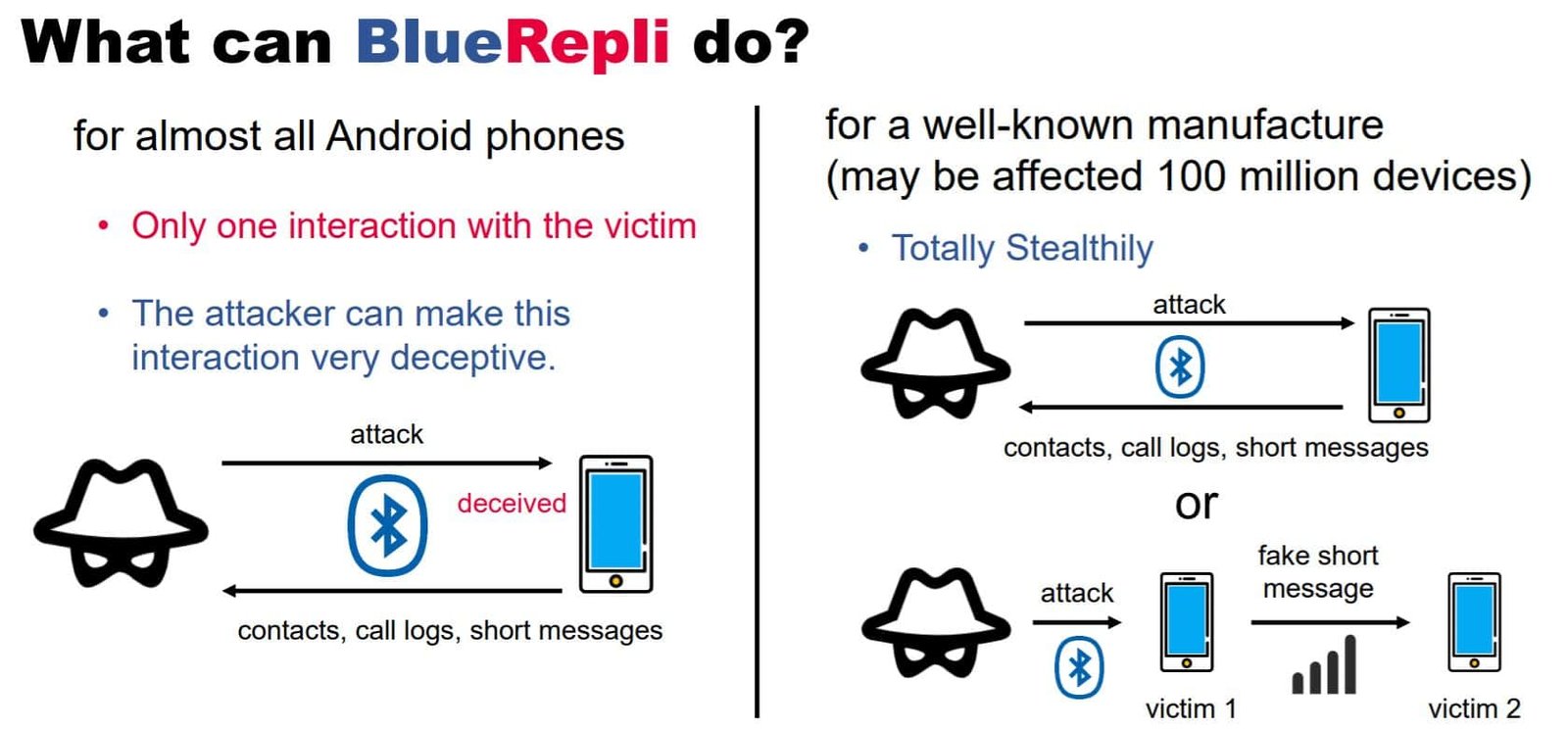
The other way to execute just works attack is through a vulnerability-based technique where the threat actor gathers two Bluetooth device addresses by scanning. The first address is the target’s Bluetooth address, while the second is the address of the Bluetooth device that has gained access to the target device, like Bluetooth headsets. The attacker tricks the target device by impersonating as the ‘headset’ by changing his address to that of the second Bluetooth address. Eventually, obtaining access to the phonebook and SMS of the host device.
“Data will be passed back to the attacker without the victim’s knowledge,” Xu said.
Safety Measures
-
Bluetooth vulnerabilities are due to the negligence of the operating system’s vendor. And once known the company quickly releases a patch to protect its users. Therefore, always keep your Android devices’ firmware up to date to update the threat definitions of the devices.
-
Many people keep their Bluetooth turn ON, even when not using it for any purpose. This always keeps them vulnerable to such attacks. So it is necessary to keep your Bluetooth, and for that case WiFi too, turned OFF to prevent an attacker to gain control over your Android device to perform his nefarious activities.


