Recently, Google Project Zero released the list of vulnerabilities exploited in 2019. Along with the first “Year In Review” report, Google also mentioned the zero-day vulnerabilities they’ve come along in the first half of 2020.
According to Google Project Zero’s security team, 11 zero-day vulnerabilities have been tracked in the first half of 2020. This takes 2020 on the track to have just as many zero-days as traced in the last year. Experts say that it may surpass the figure of 20 of 2019.
Google Project Zero
Google traced down a number of flaws in its applications used by millions of users, which could be exploited by cybercriminals. After tons of vulnerabilities were found, Google decided to form a team completely dedicated to finding flaws, not only in Google utilities but also in other applications. The new project was devised on 15 July 2014 named the GOOGLE PROJECT ZERO, on Google security blog.
The team employed by Google finds zero-day vulnerabilities. After these bugs are found, the Project Zero experts report it to the developer and make it public once the patch is released, or if 90 days pass without the patch being released. Along with the zero-day bugs, Project Zero team also illustrated how attackers exploit the bugs. This makes developers and users aware of the potential threats and their mitigations.
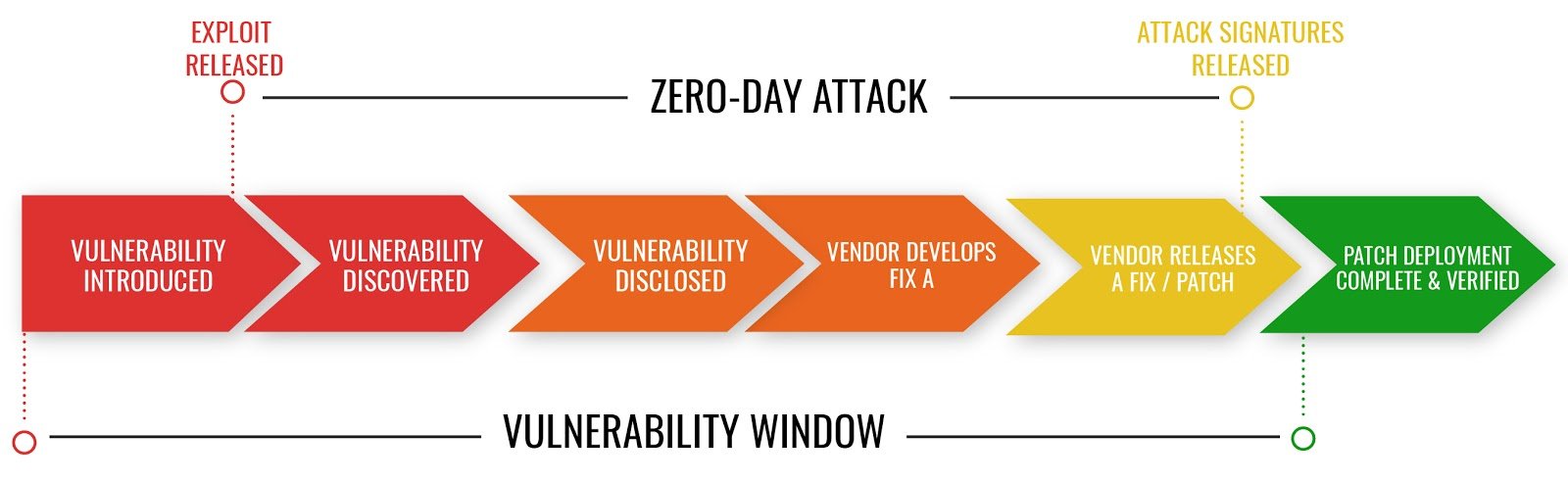
Zero-Day Vulnerability
A latest learned vulnerability is referred to as a zero-day vulnerability (or 0-day vulnerability). It also means that a fix or update of the bug is not yet released from the developer and the developer of the target application has zero days to protect its users.
But if the vendor fails to release a patch for the bug and hackers have managed to exploit the vulnerability, that is known as a zero-day attack.

In the recent report of Project Zero, Google detected eleven zero-day vulnerabilities in the wild in the first half of 2020.
Zero-Days Vulnerabilities H1 2020
1. Firefox
CVE-2019-17026
This vulnerability was a part of the another zero-day, leading to type confusion in the IonMonkey JIT compiler.
2. Internet Explorer
CVE-2020-0674
This, along with the aforementioned bug, was used by a state-backed hacking group called DarkHotel. It was believed to be controlled from the Korean peninsula, without knowing the actual state: North Korea or South Korea. The victims of the attack were directed to websites where their systems were hijacked by Gh0st RAT (Remote Access Trojan).
3. Chrome
CVE-2020-6418
The vulnerability was detected by Google’s Threat Analysis Group. But details and description of the bug were never released.
4. & 5. Trend Micro OfficeScan
CVE-2020-8467 and CVE-2020-8468
The vulnerabilities were detected in the same 2019 zero-day product which was used to hack Mitsubishi Electric. Thread Micro staff internally detected the zero-day, while investigating a previous zero-day.
6. & 7. Firefox
CVE-2020-6819 and CVE-2020-6820
Believed to be a part of a larger malicious campaign, the details of these vulnerabilities are not yet released.
8. & 9. & 10. Microsoft
CVE-2020-0938, CVE-2020-1020, and CVE-2020-1027
As other bugs, details of these zero-days were never released. These were reported to Microsoft by Google TAG.
11. Sophos XG Firewall
CVE 2020-12271
This vulnerability was found in a top-shelf firewall XG developed from a UK security firm: Sophos. A SQL injection in the firewall’s management panel allowed hackers to deploy backdoor on the infected system. This backdoor was called the Asnarok backdoor.
Sophos reported that the malware attempted to dump Ragnarok ransomware in the host systems after the zero-day was announced.
Proactive Measures
-
Always keep your system equipped with genuine antivirus software. It will work as the first line of defence.
-
In today’s time, everyday new malware infection is detected in the wild, even making your antivirus susceptible to newly updated threats. That’s why it is always important to always keep your antivirus up to date.
- Check for a zero-day vulnerability patch online once the bug is announced. Usually, developers work quickly to work on their zero-days to protect their users.
Always follow cyber ethics and establish safe and protective online habits.


