Threat issues and intelligence in blink home security cameras
We are living in an era where security is the main concern, so we opted to blink cameras for our home security issues. But today, even the blink security cameras are no more secured. They are more exposed to the possibility of being attacked. Attackers are always looking for ways into harnessing privacy. Recently in an instance, Amazon cameras have been reported to house several vulnerabilities. This time it is the Blink home security cameras.
Researchers discovered three vectors of attack in these cameras that are marketed as cost-effective options in the market.
Detailed vulnerabilities:-
One out of the three vulnerabilities that were discovered is said to be of concern to the consumers. The vulnerabilities could be exploited more randomly by a friend or contractor who secretly wants to harm you.

The very first vulnerability, that is of limited availability, involves having physical access to the device. This flaw allows attackers to control devices by providing hard-coded credentials.
The next flaw can potentially allow bad actors to launch man-in-the-middle attacks when the device is requesting for software update or network information.
The last flaw, which is believed to be the most serious of the three, involves improperly sanitized network parameters that are passed to the camera.
What does this imply?
While talking about the first flaw mentioned, which requires physical access to the device, this isn’t a major concern for everyday consumers. In order to exploit this flaw, attackers need to be able to directly interact with the device for at least a few minutes. Attackers directly or indirectly through some sort of DNS poisoning or hijacking do modify the content of the response to meet their own desires. The most common attack scenario for this flaw would be some sort of insider threat — babysitters, house or petsitters, guests, or anyone else with somewhat privileged access to your home. Security experts recommend updating your devices to the latest versions available. As always they recommend monitoring the devices connected to the home network to prevent the exploitation of the disclosed flaws. Although IoT (Internet of things) devices come with a number of useful features, the threats that accompany them are no lesser. Users must realize these issues and take necessary measures while opting for connected devices, especially at home.
The second vulnerability in home security would allow attackers to launch a man-in-the-middle attack caused due to regular request of software updates or network information.
The last flaw which is believed to be the most serious of the three can potentially allow bad actors to interfere, involves improperly sanitized network parameters that are passed to the camera.
What to do now:-
The future of security can be reinvented with spyware security products. Recently, Amazon has released updates to its Blink XT2 home security cameras after researchers discovered multiple flaws that could let nearby hackers hijack the cameras within seconds. These security flaws can be reduced with the Sync module, an extra network device that acts as a hub between the camera and the cloud. This Module allows users to divide the home into camera zones – for example, to control multiple cameras inside and outside the house, which the user may want to operate at different times. In August a Cybersecurity product that covers every aspect of an advanced, proactive security strategy including strategic and tactical threat intelligence sharing, cyber fusion, security automation and orchestration, and threat response was introduced in the market.
A detailed explanation of spyware products:-
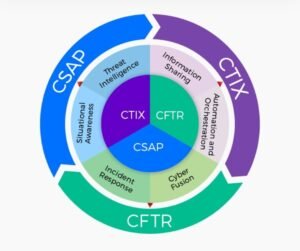
Incident response – Incidents and compromises can create serious issues for any organization whose staff are unprepared and under-equipped to handle them. Staff should identify, comfort and manage any incident that may arise to protect your organization’s private information, assets and reputation using spyware fusion and threat responses (CFTR) infrastructure.
Situational Awareness- organizations should promote cyber situational awareness with real-time, targeted and actionable alerts. Prepare teams for unexpected incidents, ensure the right informs made available to the right person at the right time.
Threat intelligence- Cyber threat intelligence and information sharing can be immensely beneficial when conducted securely, effectively and collaboratively. This will expertise to enhance your own capabilities. Gain more visibility into emerging threats and determine controls best suited to your organization.
Information sharing – any organizations should ensure that they are in house information is shared with the right audience. Real-time information sharing must collaborate with concerned organizations.
Cyber fusion – Organization require up-to-date intelligence to take on the countless threats and adversaries we face. Organizations should revolutionize their security options and incident response system with cyber fusion and threat response integration of tactical data sources to gain a holistic overview of threats and overcome them.
let’s make sure our systems and networks are safe against imminent threats. On a daily basis, some threat actors are coming back to haunt us. Let’s start with all the positive events in the cybersecurity space.
What’s happening around you to meet threat intelligence:-
1. IBM and the University of Ottawa announced the launch of a uOttawa hub to strengthen Canada’s posture towards cyber threats and attacks. The hub will pair IBM’s technology expertise in data analytics, deep learning, software, and systems with uOttawa’s research, training, and teaching strengths to meet critical cybersecurity goals.
2. The National Science Foundation has awarded a planning grant to the researchers from the University of Kansas to design a multi-institutional Center for High-Assurance Secure Systems and IoT (CHASSIS). The research center would partner with private firms in the country to enhance the security of IoT products and systems in use across sectors.
3. Researchers achieved a new crypto-cracking record with the factoring of the largest RSA key size ever computed and a matching computation of the largest-ever integer discrete logarithm. The new record includes the factoring of RSA-240, an RSA key that has 240 decimal digits and a size of 795 bits. Also, it’s the first time that records for integer factorization and discrete logarithm have been broken together.
4. The global law enforcement authorities have dismantled the infrastructure behind a remote access tool (RAT). Since first appearing in 2012, it was dubbed as the fastest remote administration tool ever created using new—and never used before—socket technology. According to Europol, the tool had more than 14,500 buyers across 124 countries and had been used to infect tens of thousands of victims.
5. The Cybersecurity and Infrastructure Security Agency (CISA) released a fresh directive that directs all federal agencies to develop and publish a vulnerability disclosure policy, allowing ethical hackers to report bugs through a defined procedure. The directive touches on various other logistics of vulnerability disclosure reports, including its handling procedures, as well as reporting requirements and metrics.


