Recently, researchers at Barracuda security firm found thousands of organisations attacked with an influx of BEC attacks during the pandemic.
With a huge hike in organisations operating online during the COVID times, a plethora of malicious attacks has come up. These attacks have included a range of ransomware attacks, spear-phishing campaigns, fraud. Millions of users are being affected worldwide. According to a study by Barracuda researchers, since April 2020 100,000 BEC attacks on nearly 6,600 organizations have been recorded. In fact, since April 1, malicious accounts have been behind 45 per cent of the BEC attacks detected.
BEC Attack
Business Email Compromise is an exploit where the attacker obtains access to a business account and impersonates as the owner or as an official of the service provider, the company is using, in order to defraud the company and its employees.
Usually, attackers create email accounts in bulk with email addresses almost identical to that of the corporate network, to force the victim to trust the email credibility. It is a rampant practice to compromise systems on a corporate network, allowing them to spread laterally in the network to establish persistence.
BEC is sometimes referred to as “man-in-the-email-attack”.
Techniques For BEC Attacks
-
Spoofing email accounts and websites: Slight variations on legitimate addresses (john.kelly@abccompany.com vs. john.kelley@abccompany.com) fool victims into thinking fake accounts are authentic.
-
Spear-phishing: Bogus emails believed to be from a trusted sender prompt victims to reveal confidential information to the BEC perpetrators.
-
Malware: Used to infiltrate networks in order to gain access to internal data and systems, especially to view legitimate email regarding the finances of the company. That information is then used to avoid raising the suspicions of any financial officer when a falsified wire transfer is submitted. Malware also lets criminals gain access to their victim’s sensitive data.

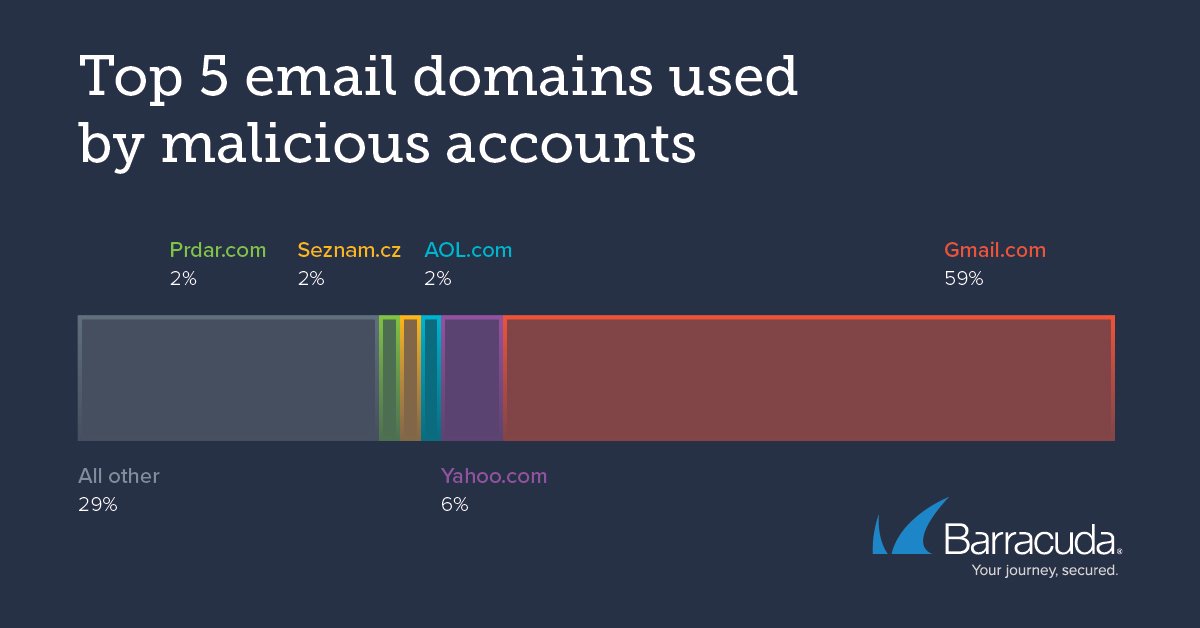
Barracuda researchers said more than 6,000 malicious accounts that use Gmail, AOL and other legitimate email services have been responsible for over 100,000 BEC attacks on nearly 6,600 organisations.
The Threat
In the recent drill of BEC exploits, attackers were seen not using their email accounts for a long time. Moreover, researchers saw that 29% of the malicious accounts were used for a 24-hour period. There are various reasons for this; malicious accounts may get suspended by the email providers against reports against them; it is easy for hackers to register new accounts easily and free-of-cost; it is also seen that cybercriminals often use an email account and leave it inactive for a long period of time and then reusing it in other attacks.
Some accounts were seen to be active over a year performing malicious attacks. However, it is not usual for hackers to reuse an account in attacks after a long break.
The attacker analyses the organisation they are going to target for their next attack. Moreover, by nature BEC is a highly targeted attack.
After decent research, cybercriminals launch emails against the employees of the organisation, impersonating an employee or a trusted partner.
These first-level emails are deployed to gain the trust of the victim. And attackers expect for replied from the victims. Therefore, these attacks are usually very low volume and highly personalized to ensure a higher chance of a reply.
The analysis shows that the same email address was used to target more than one organisation.
Cybercriminals Prefer Gmail
According to the figures, the most preferred email service to be used in the campaign is Gmail, accounting for almost 59% of the total malicious email accounts. Yahoo! is second on the list with a share of just 6%!
There’s never a permanent solution to this problem. No matter what security solution you implement you are still vulnerable.
Protect Your Organisation
-
Implement BEC protection. By leveraging artificial intelligence, unusual senders can be detected to identify BEC attacks and other frauds. This will help significantly as cybercriminals usually bypass the security gateway for emails.
-
Work with an organisation which has been affected with BEC. Because threat actors don’t use the email address to attack the same organisation twice. So this will help in blocking email addresses which were reported malicious by other organisations.
-
The most important thing is to teach your employees about spear-phishing and their harms. User training should always be a part of your security posture.
Stay Safe, Stay Updated.


