Since 2000, USB flash drives products have been on the market and their use is increasing exponentially. Secure USB devices protect the data stored on them from access by unauthorized users. As both consumers and businesses have increased demand for these drives, manufacturers are producing faster devices with greater data storage capacities. An increasing number of portable devices are used in business, such as laptops, notebooks, personal digital assistants(PDA), smartphones, USB flash drives, and other mobile devices. In particular, companies are at risk when sensitive data are stored on unsecured USB flash drives by employees who use the devices to transport data outside the office. The consequences of losing drives loaded with such information can be significant, including the loss of customer data, financial information, business plans, and other confidential information, with the associated risk of reputation damage.
Major dangers of USB drive:-
USB flash drives pose two major challenges to information system security: data leakage owing to their small size and ubiquity and system compromise through infections from computer viruses, malware, and spyware.
Remote management
In commercial environments, where most secure USB drives are used,[1] a central/remote management system may provide organizations with an additional level of IT asset control, significantly reducing the risks of a harmful data breach. This can include initial user deployment and ongoing management, password recovery, data backup, remote tracking of sensitive data and termination of any issued secure USB drives. Such management systems are available as software as a service (SaaS), where Internet connectivity is allowed, or as behind-the-firewall solutions.
USB devices spreading viruses:-
Defense Department suspends the use of USB drives as experts warn of USB-related virus outbreaks.
USB thumb drives are convenient, popular and often free–and they’re spreading viruses like sailors on shore leave. The US-CERT (Computer Emergency Response Team) issued a warning on Thursday that malicious code is increasingly propagating via USB flash drive devices. Meanwhile, the U.S. Department of Defense has temporarily banned the use of thumb drives, CDs, and other removable storage devices because of the spread of the Agent.bzt virus, a variant of the SillyFDC worm, according to Wired. We’ve seen this before with portable external storage devices. Floppy disks were the culprit in the early 1990s, followed by CDs. The fact that USB thumb drives are being used by so many people makes them an attractive target for virus writers.
“The bad guys are intentionally developing new flavors of malware designed to propagate through USB devices,” said Gunter Ollmann, chief security strategist for IBM’s ISS security division. “They are today’s floppy drives.” But USB drives are even handier. Their small size makes them easy to slip into a pocket or carry on a lanyard around your neck. A common swag item in the tech industry, they also are mainstream consumer storage devices. They literally litter my desk drawers. There are a couple of ways USB thumb drives can be used to spread viruses and other malicious software. An infected computer can spread a virus to a clean USB thumb drive that is inserted. That USB drive will then be spreading the virus onto other computers if the operating system on those machines has an AutoRun-type feature enabled. The AutoRun function in Windows launches installers and other programs automatically when a flash drive or CD is inserted. The Mac has an equivalent function, according to Ollmann. For that reason, people should disable any AutoRun features and manually launch programs when using a flash drive, he said. CERT has information about the dangers associated with AutoRun here, as well as tips specific to the safe use of USB drives here. A virus also can be embedded in what looks like a normal file on a USB device, so that even if AutoRun is disabled, the computer will become infected when the file is opened. Thumb drives aren’t the only culprits; any device that plugs into a USB port–including gadgets like lights, fans, speakers, toys, even a digital microscope–can be used to spread malware, Ollmann said. The devices can be infected during the manufacturing or supply chain process if quality control measures are not adequate, he said.
In addition to disabling AutoRun, Ollmann suggests that people use an antivirus tool to scan their USB devices before opening any files from them and be cautious with files on devices even if they come from trusted sources. There’s also the danger that the small devices can be lost, exposing the data on them to whoever happens to find them. A Swedish soldier was recently convicted of negligence after leaving a USB flash drive with classified information on it in a computer at a Stockholm university, according to an Associated Press report. And a British tax agency was forced to shut down its Web site after a contractor lost a flash drive containing confidential passwords and source code in a pub parking lot last month.
Solutions:-
Since the security of the physical drive cannot be guaranteed without compromising the benefits of portability, security measures are primarily devoted to making the data on a compromised drive inaccessible to unauthorized users and unauthorized processes, such as may be executed by malware. One common approach is to encrypt the data for storage and routinely scan USB flash drives for computer viruses, malware and spyware with an antivirus program, although other methods are possible.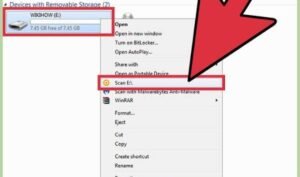
How to Remove an Autorun Virus:
- Open your flash drive.
- Delete the autorun.inf application.
- Restart the computer and then open the Command Prompt.
- Type the drive letter of the USB and press “Enter”.
- Type “attrib -r -h -s autorun.inf” and press “Enter”.
- Restart the computer.
So, feel free to carry a USB memory stick, but be very careful where you put it.


