Recent Investigation alerts of a scam that clones an authorized service granting private, encrypted, and self-destructive messages, to modify BTC addresses that eventually steals funds from innocent dupes.
For the past few years, a site named Privnotes.com has been imitating Privnote.com. Privnote is a legitimate, free message service provider that offers private, encrypted messages that automatically self destruct its content after being read. The intimate clone “Privnotes” automatically sorts out messages containing bitcoin addresses and changes it with its own bitcoin address. This Event eventually tricks the user into clicking the phishing link rather than the legitimate link. Usually, it is found that the Internet protocol (IP) addresses of the sender and receiver of the message are not identical.
Harvesting Bitcoins By Altering Addresses
Usually, the users were using the authorized service Privnote.com (without the “s”). But later on, a new clone site comprising the letter “s” at its domain tried to impersonate the user. The clone site was running the same services as that of the original. It’s not hard to observe why both the sites appear to be the same. It is confusingly similar in name and appearance. Also, It comes up second in Google search results for the term “privnote.” The clone site “privnotes.com” runs a misleading paid ad for “Privnote” that tricks the user into clicking into the illegitimate website.

The legitimate website “Privnote.com” uses a chipper that encrypts all messages so that even the Privnote itself cannot read or alter the contents of the message. One can not directly send the messages. Whenever you create a message, it generates a link. When that following link is visited, the employed service warns the user that the message shall be deleted once read.
But the security personnel of Privnote.com reported that the clone phishing site did not completely implement encryption and can read and modify all messages sent by users.
“It is very simple to check that the note in privnoteS is sent unencrypted in plain text,” Privnote.com explained in a February 2020 message, responding to inquiries from KrebsOnSecurity. “Moreover, it doesn’t enforce any kind of decryption key when opening a note and the key after # in the URL can be replaced by arbitrary characters and the note will still open.”
But that’s not the complete overview. Security analyst said that the phishing site comes along with an automated script that searches messages comprising of bitcoin addresses. Later on, those addresses are replaced by any bitcoin addresses found with its own bitcoin address. The script apparently only modifies messages if the note is opened from a different Internet address than the one that composed the address.
Insights of message contents:
Below illustrated is an example of the scenario. The subsequent message was written at Privnotes.com from a computer with an Internet protocol (IP) address in Bangkok, with the message composed as “please send money to bc1qar0srrr7xfkvy5l643lydnw9re59gtzzwf5mdq thanks”:
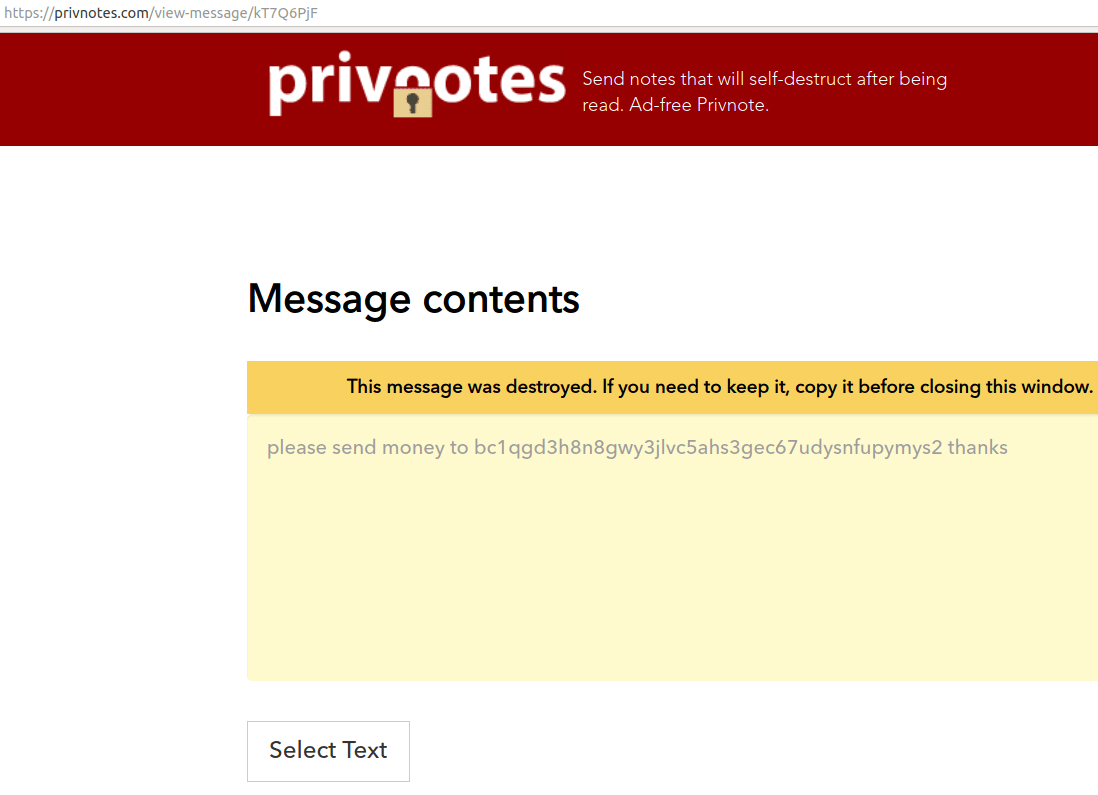
The test message mentioned above is frequently phishing users of the authorized encrypted message service privnote.com. Try to observe the bitcoin address keenly; it differs completely from the previous ones.
When the security personnel visited the link on Privnotes.com generated by clicking the “create note” button on the above page. This time from a different computer with an Internet address in Newyork. When keenly observed, you see a different bitcoin address, comprising the first four characters as same from the previous address.
Several other Tests reportedly proved that the bitcoin restraining script does not resemble to modify message body contents if the sender and receiver’s IP addresses are found to be identical.
One of the security experts, Allison Nixon, said that the script replaces the first occurrence of a bitcoin address if it’s repeated within a message, and the site stops replacing a wallet address when it is then consequently sent over multiple messages. Apart from these, the phone service used on the clone site also seeks some other sensitive data, which makes it more prone to ordinary people.
Conclusion:
In the future, you may want to opt for a legitimate encrypted message service, just like Privnote.com. This scam would be a great reminder for you to pay extra attention while traversing through search engines. One of the best approaches would be to bookmark authentic sites, and rely exclusively on those instead.



