Around the time when tensions between the Iran and U.S. started mounting last month(December 19), Saudi Arabia authorities discovered a new variant of data-wiping malware named ‘Dustman’. As per recent reports, cybersecurity analysts suspect it originated with Iranian hackers. The malware was deployed by the attackers against an unnamed target on Dec. 29 with “urgency,” marked. In the rush to execute their malware and in other related processes they left clues behind on the victim network, according to a technical report from Saudi Arabia’s National Cybersecurity Authority (NCA) obtained by CyberScoop. While the National Cybersecurity Authority(NCA) advisory doesn’t straightforwardly identify the culprit suspected in the attack, it does suggest that the work is of state-sponsored hackers. Analysts familiar with the attack told CyberScoop that the activity carries technical similarities to previous hacking out of Iran. As first reported by Yahoo News, this advisory is the latest sign that Iranian computer operatives are apparently using data-wiping malware to disrupt organizations in the Middle East. Cybersecurity analysts declined to be named because of the sensitivity of the issue but mentioned that it is in line with the previous activities seen from groups attributed to Iran. Yet in this bug, the damage has been limited compared to previous years due to NCA’s heavy involvement with the target at very early stages. Although the Bapco cyber attack doesn’t appear to be connected to the current hiked US-Iranian political tensions of US-Iranian. Bapco might be aimed to show Iran’s advanced technical capabilities in launching destructive cyber-attacks. As the conflict has become more anxious, the private sector security experts and the U.S. officials have warned of Iran’s ability to strike back online. Iranian operatives could, carry out data-destroying hacks, or conduct cyber imposition to enable a better understanding of our strategic direction and policy-making, the Department of Homeland Security’s cybersecurity division said on this Monday. Saudi Arabia being a U.S. ally could also be a target organization. According to the U.S. officials, A 2012 cyberattack on Saudi Aramco that disabled tens of thousands of computers at the state-owned oil giant relied on Shamoon wiper malware, which was possibly designed by Iran. The last month’s incident was the latest reminder that the threat has not become less severe. New Wiper Malware ‘Dustman’ Takes on Bapso which is a Bahrain’s National Oil Company. The attack closely favors the modus operandi of known Iranian state-sponsored hackers. Saudi CNA officials stated that the company’s VPN servers were the point of entry.
Cybersecurity analysts declined to be named because of the sensitivity of the issue but mentioned that it is in line with the previous activities seen from groups attributed to Iran. Yet in this bug, the damage has been limited compared to previous years due to NCA’s heavy involvement with the target at very early stages. Although the Bapco cyber attack doesn’t appear to be connected to the current hiked US-Iranian political tensions of US-Iranian. Bapco might be aimed to show Iran’s advanced technical capabilities in launching destructive cyber-attacks. As the conflict has become more anxious, the private sector security experts and the U.S. officials have warned of Iran’s ability to strike back online. Iranian operatives could, carry out data-destroying hacks, or conduct cyber imposition to enable a better understanding of our strategic direction and policy-making, the Department of Homeland Security’s cybersecurity division said on this Monday. Saudi Arabia being a U.S. ally could also be a target organization. According to the U.S. officials, A 2012 cyberattack on Saudi Aramco that disabled tens of thousands of computers at the state-owned oil giant relied on Shamoon wiper malware, which was possibly designed by Iran. The last month’s incident was the latest reminder that the threat has not become less severe. New Wiper Malware ‘Dustman’ Takes on Bapso which is a Bahrain’s National Oil Company. The attack closely favors the modus operandi of known Iranian state-sponsored hackers. Saudi CNA officials stated that the company’s VPN servers were the point of entry.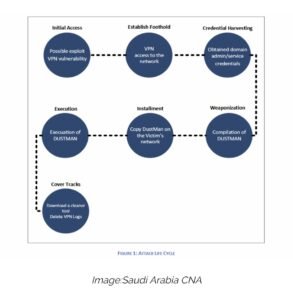
The actual working of the dustman
On December 29, the malware used in the attack, contains multiple malicious files, including a wiper, which destroys data, is dubbed as Dustman. Saudi authorities described Dustman as a variant of malware that had been used in data-wiping attacks against industrial organizations in the Middle East late last year. IBM uncovered that attack attributed it to APT34, a hacking group associated with the Iranian government. The Saudis assume that the hackers may have broken into the target network by exploiting a known vulnerability in a virtual private network application that was disclosed last July. From there, the hackers took help and accessed domain with administrative accounts on the victim’s network and eventually executed this malware, the Dustman malware. This attack is inconsistent with other known destructive attacks as they are usually tested before being deployed.” Though thinks we’re not pretty clear. It was not immediately confirmed if other organizations were also targeted by Dustman malware. The NCA could not be reached for any clear comment on the issue. Bapco attack communicated the use of this new strain of malware which could be more advanced and an upgraded version of the ZeroCleare wiper which was first discovered in September 2019.
Dustman, the data-wiping malware
Linked to the Tehran regime, Dustman is viewed as the third different data-wiping malware linked to the Tehran regime. IBM X-Force has earlier linked Iranian hackers with ZeroCleare, which, in turn, had multiple code similarities with the original Shamoon wiper malware. There was a common component similarity between all three strains is EldoS RawDisk. It is a legitimate software toolkit for early interaction with disks, files, and partitions. The only noticeable difference in these attacks was that these malware strains are used with different techniques and exploits to advance initial access to the admin-level. These admin levels are from where they unpack and propel the EldoS RawDisk utility to wipe data on infected hosts. The good part was that the attack did not have the long-lasting effect hackers might have wanted.


