Third-party extensions have always been a threat to google chrome users. Recently, security personnel proclaimed a proof-of-concept on dangerous Chrome extensions that transforms Chrome browsers into proxy bots and allow hackers to navigate through the web using a compromised user’s connection.
The tool was developed by security researcher Matthew Bryant and is named “CursedChrome.” It is available on GitHub as an open-source project.
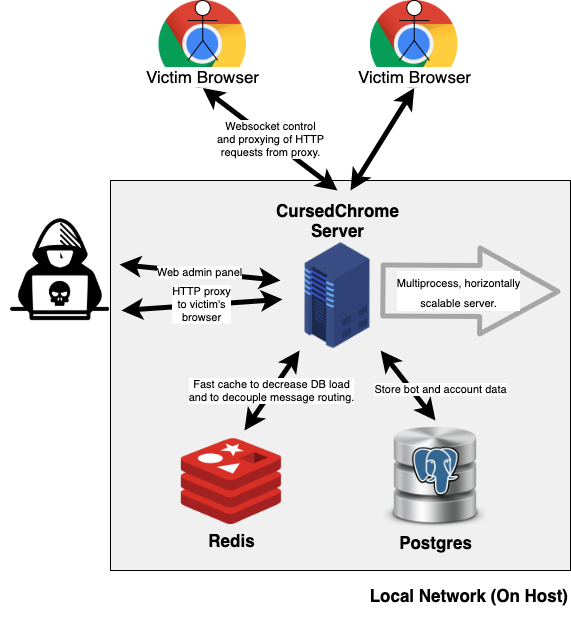
Internally, CursedChrome is composed of two different mechanisms:
-
A client-side component (the Chrome extension itself)
-
A server-side counterpart (control server where all CursedChrome bots report)
What is CursedChrome?
CursedChrome is a third-party browser extension tool that implants into the victim’s Chrome browsers and escalates fully-functional HTTP proxies. By using the proxies, this tool allows the attacker to browse the web authenticated as your victim for all of their websites.
A project like CursedChrome is a boon tool for hackers.
Affects of CursedChrome:
Once the extension is installed on the chrome browsers, then it allows the intruder to log into the control panel and helps to build a connection between infected host. The bond within the CursedChrome extension and the control panel is a mere WebSocket connection that operates as a standard HTTP reverse proxy.
This indicates that if the attacker connects to an infected host, then, they have access to navigate through the web using the infected browser, and by doing so, they can steal session cookies which further results to log in sessions and access forbidden domains, such as intranets or enterprise apps.
Besides, CursedChrome is potentially an ideal tool for pen-testers. That’s the reason why it is backed by some of the cyber-security community, who claimed that releasing something like CursedChrome does nothing but has degraded the motto for attackers to develop their own malicious tools in the future.
Purpose of Creating CursedChrome
However, in a recent interview, Bryant said that the motive of building such a tool was to engage more participation from pentesters to develop their own innovative tools.
“I open-sourced the code because I want other professional red teamers and pen-testers to be able to simulate the ‘malicious browser-extension’ scenario accurately,” Bryant said
Talking about Red teamers, he referred them as a cyber-security professional who gets paid to break into companies. Apart, they play a very crucial role in maintaining decency and keep out all the unethical web activities.
“Open-sourcing tooling is important for red teams for the same reasons as any other job: it saves time for the teams at different companies from having to rewrite everything whenever they do a red team or pentest. It’s actually doubly important for us because pen-testers and red teamers work on extremely tight timelines,” Bryant said.
The researcher also told that CursedChrome is nothing that an attacker couldn’t have built themselves. The project works on already-existing technologies and doesn’t bring any innovation to the table.
“Similar tools such as Cobalt Strike’s ‘browser pivot’ (for Internet Explorer) and the open-source BeEF framework have existed for years, and the technical details of how to perform this attack are freely available online,” Bryant said.
Furthermore, Bryant said that he is not afraid regarding hackers breaching and misusing this tool because Weaponizing CursedChrome requires that attackers either.
-
Host the extension on Chrome’s Web Store.
-
Install it via an enterprise policy or through Chrome’s developer mode.
The first case would definitely not work out because Google may index through its “web store” and eliminate the extension if found as a threat while the second scenario requires authentication to the company’s intranet server. By this point, hacker already has full authentic control and can access everything. So the use of CursedChrome becomes useless. Isn’t it.

FIX TO THIS PROBLEM.
Nowadays, most of the enterprises us more web-based tools, browser extensions are more powerful than ever. Void of any rules and installation of any malicious extension can create a loophole in the system that allows hackers to bypass firewalls. It becomes indispensable to raise awareness of just what level of access you’re granting when you install a random extension for your browser. To counter such problems, researchers have created a new web-based tool, named Chrome Galvanizer. It can be installed on all workstations. Primarily, this tool is designed for IT administrators so that they could allow or block Chrome extensions from accessing malicious URLs. Thus, in this way, even if the user installs a malicious Chrome extension, the extension won’t be able to steal user credentials within the site and web server.



