Context
Apple is considered as the most secure and reliable support system. Although, from the last few years, it has been a potential target for cyber crooks. An Indian stack developer and bug bounter “Bhavuk Jain” in April discovered a dangerous vulnerability on Apple’s interface. The vulnerability was potentially able to take over the user accounts. The vulnerability used ‘Sign in with Apple’ service as a mediator between third-party applications. The bug didn’t implement additional security measures.
On a bug bounty program, Apple recently paid India bug bounty researcher Bhavuk Jain an enormous $100,000 bug bounty for proclaiming a highly perilous vulnerability concerning its ‘Sign in with Apple‘ service. As of now, the vulnerability has been patched. In its initial stage, the vulnerability had allowed remote intruders to bypass user authentication and potentially take control over Apple users’ accounts on third-party services. Besides, it had also targeted the apps that have been registered using ‘Sign in with Apple’ option provided on its web service.
Sign in with Apple
Sign in with Apple’s feature was launched last year at Apple’s WWDC conference. The main objective of this campaign was to protect privacy by preserving login authenticity. The newly introduced service allowed users to integrate their Apple accounts with Third-party apps without disclosing their actual Apple IDs. The Indian cyber enthusiasts reported that the vulnerability was discovered during the traversal of user authentication service. He found that the client-side was not responding securely to the authentication servers.
Let me explain the mechanism. Every time a user authenticates through a “sign in with Apple” service, it generates JSON Web Token (JWT) that contains user credential information that is further used by the third-party applications to confirm the identity of the user. Bhavuk mentioned that Apple asks users to log in to their Apple account before initiating the request, it was unable to validate whether if it is the same person is inquiring JSON Web Token (JWT) in the next step from its authentication server.
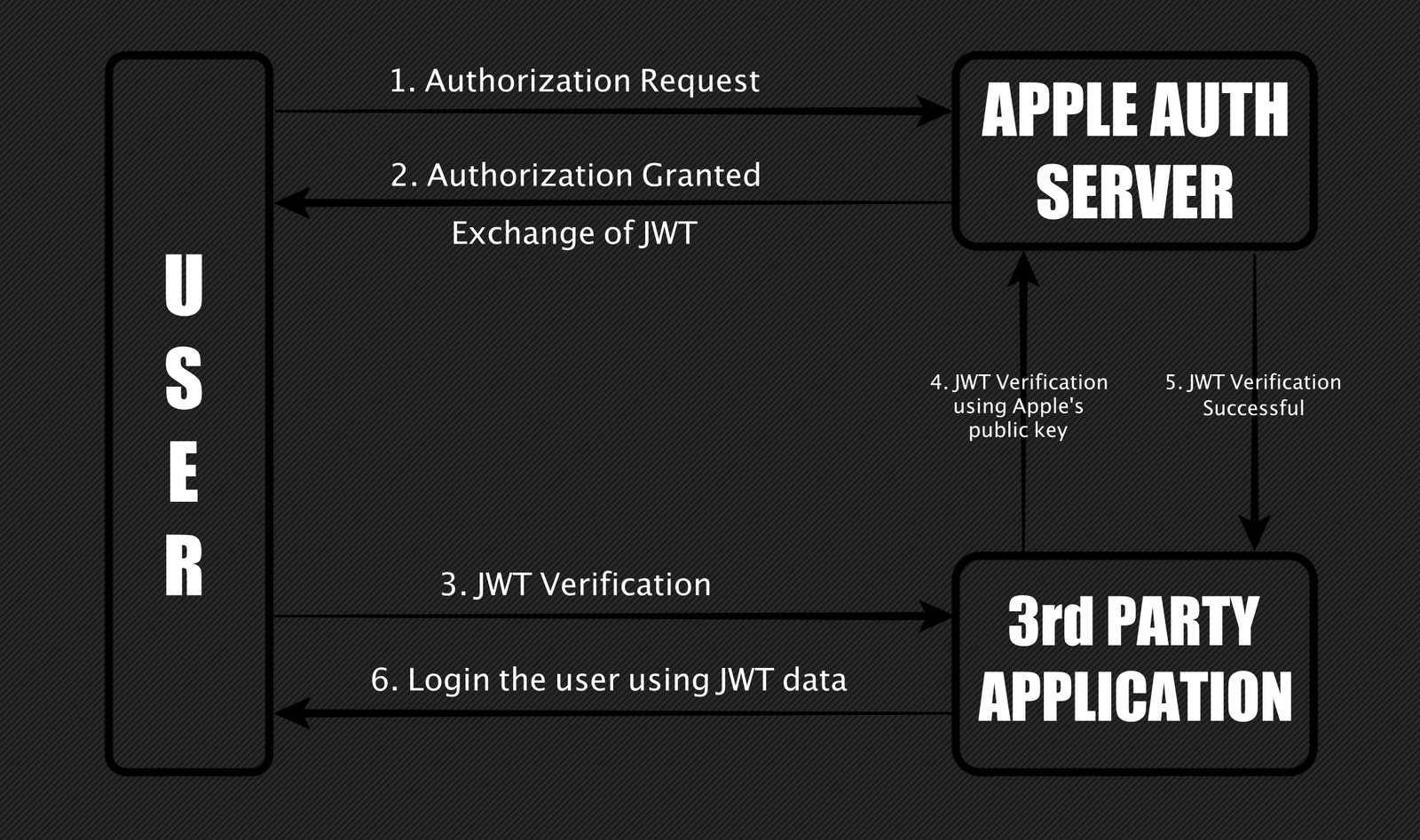
Therefore, the loophole on its validation part resulted in an attacker compromising the user accounts. It allowed the hacker to provide a separate Apple user ID belonging to a victim that tricked the server into generating JWT payload that was validating attacker to sign in into a third-party service with the victim’s identity.
Cybersecurity personnel confirmed that the bug operated even if you prefer to hide your email ID from the third-party services. The consequence of this vulnerability was considerably decisive as it could have allowed a full account takeover.
Basically, It was a server-side bug of Apple. Besides, researchers also claim that some services of applications offering ‘Sign in with Apple’ to their users might have already been using a two-factor authentication that could potentially mitigate the issue for their customers. Bhavuk had reported the vulnerability to the Apple security team last month, and as a result, the company has now patched the vulnerability and has also ensured the legitimacy of authorized users.

BUG Findings:
“I found I could request JWTs for any Email ID from Apple, and when the signature of these tokens was verified using Apple’s public key, they showed as valid. This means an attacker could forge a JWT by linking any Email ID and gaining access to the victim’s account,” Bhavuk said.
Sample Request (2nd step)
POST /XXXX/XXXX HTTP/1.1
Host: appleid.apple.com
{“email”:”contact@bhavukjxxxxx.com”}
Here on passing any email, Apple generated a valid JWT (id_token) for that particular Email ID.
- Sample Response
{“authorization”{
“id_token” : eyJraWQiOiJlWGF1bm1MIiwiYWxnIjoiUlMyNTYifQ.XXXXX.XXXXX”, “grant_code” : “XXX.0.nzr.XXXX”, “scope” : [ “name”, “email” ]
},
“authorizedData” : { “userId” : “XXX.XXXXX.XXXX” }, “consentRequired” : false
}
Conclusion
Before the vulnerability was made public, many developers had already integrated their accounts with “Sign in with Apple” because it is compulsory for applications that support other social logins. The few social platforms that use Sign in with Apple are Dropbox, Spotify, Airbnb, Giphy. The mentioned applications were not tested but it may be possible that this could have been vulnerable too. But eventually, it did not happen because of the other security measures practised while verifying a user.
Apple also performed a security audit to determine if there were any misuse or compromised accounts based on this vulnerability.



