FOREWORD
SIM cards are no longer safe. In the wake of various SIM-swap assaults, like the forebodingly named Simjacker, another and much greater risk has been found by specialists at Ginno Security Lab named WIBattack, which misuses a flaw in the Wireless Internet Browser (WIB). This flaw found on some SIM cards allows the perpetrator to assume control of the individual’s smart phone from anywhere on the planet.It can enable pernicious on-screen characters to follow a clients’ gadgets by mishandling little-known applications running on SIM cards. This new attack termed WIBattack is similar to Simjacker, an attack uncovered by the security firm, AdaptiveMobile. The fundamental framework for both these attacks is very similar. They grant access to common directives, with the exception being that they target different applications running on the SIM cards. Predominantly, Simjacker runs directions against the S@T Browser application, while WIBattack sends directions to the Wireless Internet Browser (WIB) application. Both are Java applets that versatile telcos introduce on SIM cards they give to their clients. The purpose behind these applications is to permit remote administration for client gadgets and their versatile memberships.
WIBATTACK
In a report, AdaptiveMobile claimed that it discovered a “privately owned business that works with governments” was sending rebel directions to S@T Browser applications running on SIM cards to follow or trace people which lead to the Simjacker controversy. After that, Security analysts from Ginno Security Labs said that the WIB application was also prone to similar attacks, yet there was no sign of any attacks as of then. However, WIBattack was first discovered in 2015,but it wasn’t openly unveiled. As the defect was difficult to fix and in the fear that it could be mishandled by threat actors who could remotely assume control over the mobile phones using vulnerable SIMs,it was not made public. It was assumed that WIBattack was lead by a group of talented assailants, who could enable a risk on-screen character which could trace a victims location, start telephone calls or tune in to close by discussions.
On account of both S@T and WIB applications, assailants could send a uniquely designed double SMS that would execute STK (SIM Toolkit) directions on SIM cards. The directions upheld on the WIB application are similar to the ones bolstered by the S@T Browser, which are: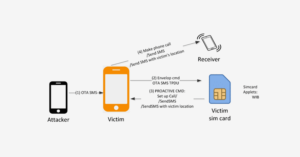
• Retrieve information on the clients location/position
• Make fake calls
• Send fake messages on behalf of the client
• Perform denial of service by incapacitating the SIM card
• Dispatch web program with a particular URL to redirect them to phishing sites
HOW IT IS DONE?
(1) The Assailant sends a malevolent OTA SMS to the client’s telephone number. The OTA SMS contains WIB directives like, SETUP CALL, SEND SMS, PROVIDE LOCATION INFO, and so on.
(2) Right after receiving the OTA SMS, Baseband Operating System of the client’s cell phone uses ENVELOP COMMAND to advance directives of the OTA SMS to the WIB program in the individual’s sim card. This is very different from the methodology of receiving normal text messages. This technique of OTA SMS is discreetly dealt within the Baseband working framework. It is carried out in such a manner that it doesn’t not raise any alarm in the Baseband Operating System of different phones. Neither feature phones nor smartphone raise alarm against the technique of OTA SMS in the form of: no ringing, no vibration, no recognition from clients.
(3) WIB web browser then pursues the WIB directions inside the OTA SMS and sends the PROACTIVE COMMAND to the client’s cell phone, for example, SETUP CALL, SEND SMS, and PROVIDE LOCATION INFO.
(4) The client’s cell phone then follows the PROACTIVE COMMAND received from the individual’s simcard to perform the corresponding actions , for example, make a telephone call, send a sms to whatever telephone number an assailant needs.
PRECAUTIONS
It has been assessed that the number of gadgets running SIM cards with a WIB application is at many millions. Yet, the estimations that Simjacker and WIBattack sway a huge number of SIM cards may not be exact. The SRLabs, a notable master in the field of Telco security, recently created two applications named SIMTester and SnoopSnitch. B Regardless of whether the two SIM card applications are installed or not, the SRLabs group said that it doesn’t consequently mean the SIM card is vulnerable to attacks. To be exploitable, aggressors would need to be able to send OTA SMS messages to the two applications, something that Telcos can hinder by empowering security measures within the two applications.
The first is a work area application that clients can install to test their SIM cards for security defects. The second is an Android application that keeps running on established gadgets with Qualcomm chipsets and which can test cell phones for different SIM, versatile system, and OS security imperfections. Scientists utilized telemetry from both applications to research the broadness of the WIBattack vulnerabilities. Altogether, they got information from 800 SIM card tests by means of the SIMTest application, from everywhere across the globe. The outcomes uncovered that most portable telcos don’t use the WIB browser any longer. These outcomes imply that most clients today are sheltered from these dangers, which is confirmed through private discussions that an anonymous journalist had with mobile security specialists, who said that only a handful bunch of suppliers across the world ship SIM cards with these two applications, for the most part situated in Eastern Europe and Latin America.
SIM card operators can address the SIM security issues in two different ways: By evacuating the SIM applet vulnerabilities, or by blocking parallel SMS on their systems. The two methodologies accompany restrictions, and a mix of both is suggested as best measure to deal with it. These are recommendations similar to what were given by by the SRLabs and was implemented by many, yet not by most of the mobile networks. Clients can only with significant effort secure themselves from such attacks since SMS conveyance and SIM configuration are outside of their control. Clients can anyway check whether a SIM is under attack or not, by running the SIMTester or SnoopSnitch on an established Android mobile phone.
Similar to the WIBattacks, there has been the emergence of a new Malvertising threat group named eGobbler which exploits a zero-day security imperfection in WebKit that Google still hasn’t been able to fix. Want to know more about ? To know more, visit https://blarrow.tech/wibattack-a-second-attempt-at-sim-swap/



