About:
Rapid Increase in cyber threats are encountered in 2020, ongoing vogue of attacks continues which has now put a reputed Firewall manufacturer in uncertainty. Users of a widely commercially used firewall from Sophos have been put under a zero-day exploit that was configured to steal usernames, cryptographically protected passwords, and other sensitive data. Research team at Sophos-XG firewall first diagnosed zero-day exploit on late Wednesday, April 22, after it received a report from one of its customers. The customer reported observing”a suspicious field value visible in the control panel management interface.”
What is Sophos-XG firewall?
Sophos firewall is next-generation network protection utility program having deep insights in your private network. It instantly identifies compromised system, malicious payloads, advanced threats and your riskiest users. With its alarming indicator It brings a fresh new approach to the way you manage a firewall, respond to threats, and monitor what’s happening on your network. User can instantly see how the system is performing and how the network being used. It has a built-in comprehensive on box reporting having its own risk assessment tools. It easily identifies riskiest user, malicious program before they become a real potential issue.

What are ZERO-DAY exploits?
Zero day is a (software, network) security flaw that is undiagnosed by the software vendor. Until the vulnerability is mitigated, hackers can traverse the exploit to adversely affect computer programs, data, additional computers or a network. The term zero day may refer to the vulnerability or flawy. Basically, it’s an attack that has zero days between the time the vulnerability is discovered and the first attack. Once a zero-day vulnerability has been made public, it is known as n-day or one-day vulnerability.
Recently zoom zero-day exploits were sold on dark web. Basically, the exploit is not made public to all until some heavy amount is paid to the hacker. These monetary transaction does not take place on surface web rather it transpires on Deep web.
What is SQL injection?
SQL injection is a web security vulnerability that allows an intruder to play with the queries that an application makes to its database.SQL injection can potentially exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. Basically,It can take over and control the complete mapping of datasets.
Mainly SQL injection is performed over web servers with such URL:
Format specifier: (php?id=x)
Example:
http://newspaper.com/items.php?id=2
Ideology:
Sophos claims, ‘The intruders had previously used an unknown SQL injection vulnerability to gain access to exposed Sophos-XG devices’.
Firewall had administrative privilege and access over HTTPS ports and other file transfer port which allowed Intruders to target Sophos XG Firewall devices that had their administration (HTTPS service) or the User Portal control panel exposed on the internet.
Sophos diagnosed the exploit and said that the hackers used the SQL injection vulnerability to download a payload on the device. This payload then stole files from the XG Firewall and upload it on the hacker’s machine. Stolen data could inherit usernames and encrypted hashed passwords for the firewall device admin, for the firewall portal admins, and user accounts used for remote access to the device. Stolen files also includes the firewall’s license and serial number, and user emails.
Security research team at Sophos firewall said that during its investigation, it did not find any evidence that hackers could potentially use the stolen passwords to access XG Firewall devices, or anything beyond the firewall, on its customers’ internal networks. Sophos researchers named the malware Asnarok. A well detailed, step by step analysis and presentation of the malware’s features and modus operandi was published here.
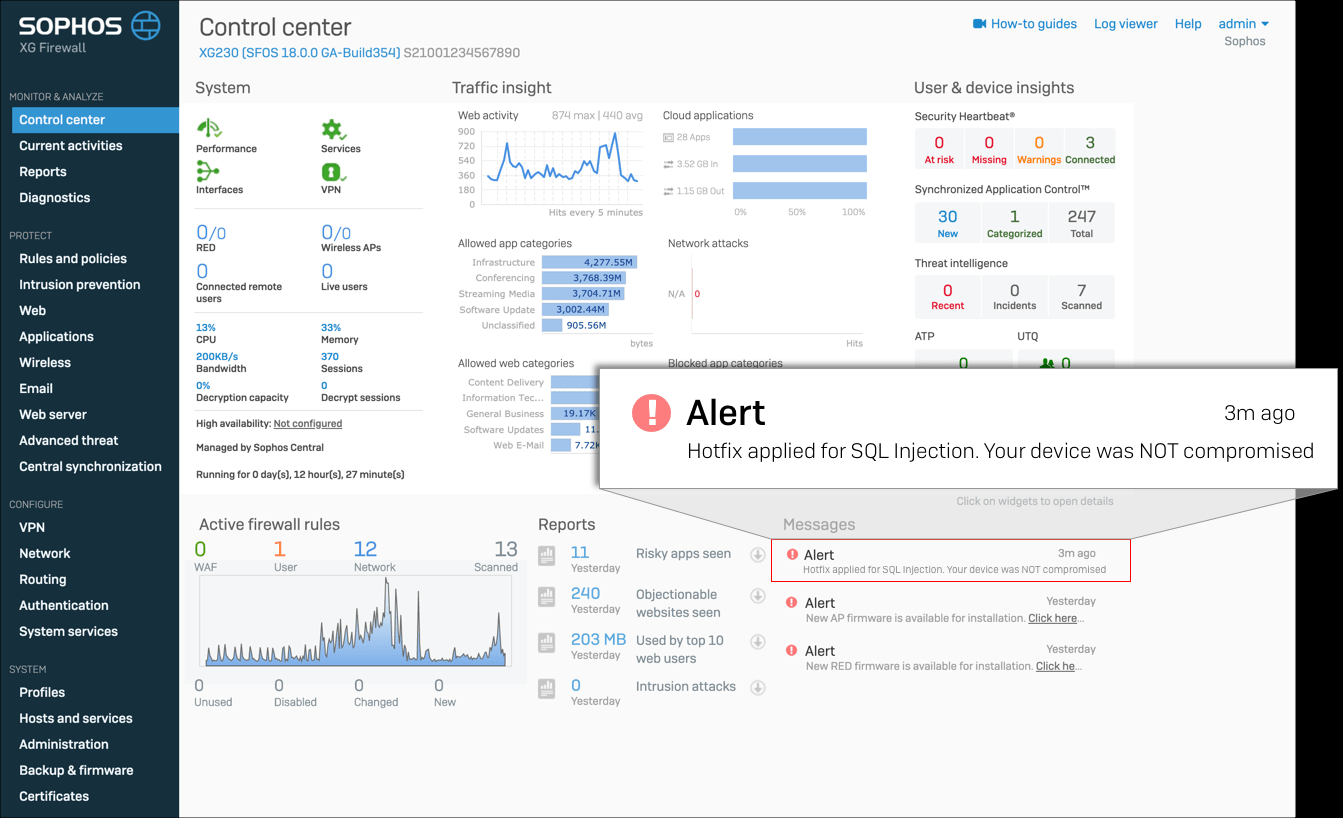
Preventions:
A new update has been pushed over customer devices which has patched the existing vulnerability. The security update will also add a special box in the XG Firewall control panel to let device owners know if their device has been compromised.
For the affected clients Sophos has issued some guidelines and instructions which need to be followed to avoid any further complicacy.
- Reset portal administrator and device administrator accounts to avoid further complicacy.
- Reboot the firewall XG devices
- Reset passwords for all local user accounts
- Since the harvested passwords were in hashed format, it is recommended that passwords are reset for any accounts where the firewall administrative credentials might have been reused.



