Ransomware is a devastating problem, and it’s difficult for the victims to know, paying up will help them to regain access to their encrypted files. And anyone with important data stored is at risk, including education sectors, government and law enforcement, healthcare institutions, or even individual system operators. In this article, you will find everything you need to know about the latest ransomware, HILDACRYPT.
Contents:
- What is HILDACRYPT?
- Spread of .HILDA
- Delivering HILDACRYPT
- Removal of .HILDA
- Precautions to counter HILDACRYPT

What is HILDACRYPT?
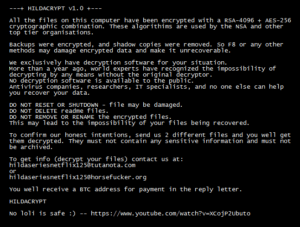
HILDACRYPT, a malicious software ransomware that is designed to encrypt files and prevent victims from accessing them unless they pay a ransom. It’s a disastrous PC threat from the Ransomware family and can intrude on any Windows machine, including XP, Vista, 7.8, and the lastest 10. Once the virus is inside your computer, it can conduct endless malignant activities that downgrade your system performance. The ransomware changes extensions of encrypted files to “.HILDA“, for example,it renames “1.jpg” to “1.jpg.HILDA!”. Ransom notes are created names as “READ_IT.TXT,” and victims can find folders that contain encrypted files. .HILDA file virus is another violet and nasty computer malware.
This malware virus can easily alter your computer settings and disable your security-related programs. It also encrypts your data using a powerful encryption algorithm and makes them inaccessible. When you open the ransom file left by .HILDA File Virus, you will discover that your data is encrypted to cheat money from you. In order to unlock through private decryption generated from your system, the attackers ask you to encrypt files through a powerful algorithm. You will also be asked to contact the hackers about the ransom amount and proof of decryption code.
The ransom amount/fees asked to pay are in the form of Bitcoin, as it cannot be traced. Further time is given for transferring the money, and if the money is not paid in said time, the attackers threaten to delete your decryption key — makers of. HILDA virus doesn’t care about your files, and they might not even reply to you after getting the money.
Spread of .HILDA:
The malicious virus is a dangerous malware that is majorly spread through spam emails with attachments. You can get victimized by this virus when you download freeware programs, cracked illegal patches from suspicious websites. The threat can also slip into your system from torrent websites regularly or from misleading ads that redirect your browser to shady websites. These are some ways through which vulnerable malware can be spread as they often use phishing sites.
Once the .HILDA has started the execution of its built-in sequence of dangerous commands, specific hacker instructions with various actions are followed depending on the considerations of the system. HildaCrypt v.10 paralyzes the whole system when it encrypts your photos, documents, archives, projects, and sometimes in most cases, the years of work get permanently damaged.
HildaCrypt ransomware was created for educational purposes and the sake of curiosity. According to the developers of ransomware, the development was for fun and now the spread of it has increased. This ransomware has also been packaged and made into versions by other hackers.
The recovering process of files that have been encrypted by HildaCrypt could be tricky and time-consuming, but you need not pay hefty ransom money when you have recent backup files to restore data. You will need to remove the infection first, or it is going to keep encrypting your files. You can even store the encrypted files on any cloud server and wait for any free decryptor to release. Reinstalling the Windows or formatting your system will erase the chances of recovering your file, so instead, use a powerful anti-malware software to remove the infection.
Delivering of HILDACRYPT:
The .HILDA virus is the latest discovered threat that appears to be made entirely by hacking groups. We have listed below some of the distribution methods for the ransomware:
- Email Phishing: Crafted emails used to manipulate victims, supposing that they have received a legitimate message and interacting with it in any form, will deliver the virus.
- Browser Plugins: One of the most popular carriers, ‘hijacker,’ used to upload extension repositories or malware sites with fake reviews and to aim to convince the visitor into installing them.
- Phishing Sites: Sites that fool the visitors into getting convinced that they are accessing safe addresses.
- File-Sharing Networks: Networks such as BitTorrent are widely used to spread pirate and virus-infected files.
- File Carries: Made by using legitimate installer and using embedded data for execution. The other type includes integrating macros into document formats like spreadsheets, presentations, databases, and text files.
When the virus infection starts on a system, the threat begins a built-in sequence in accordance. A critical procedure is masking the engine by using a double extension. Most victims are not able to distinguish them and don’t pay attention to the fact that an innocent-looking file is actually a malware. The virus makes it difficult for the victim to restore their data by modifying or removing backups.
The .HILDA virus spreads infections in various ways. It distributes its payload file on social media and file-sharing services. .HILDA virus is a cryptovirus programmed to encrypt user data. directly after all modules have finished running in their prescribed order the lock screen will launch an application framework that will prevent the users from interacting with their computers. The virus could be set to erase all the Shadow Volume Copies from the Windows operating system.
Removal of .HILDA:
HildaCrypt is spread by trojans that are downloaded accidentally. It downloads and stores an executable 5021052.exe to %TEMP% folder. It is executed using some system parameters and adding Registry keys of its own. If a received email is irrelevant and is sent from an unknown or suspicious address and contains an attachment, then the file attached to it should not be opened. Below listed are the manual removal processes:
- Start PC in Safe mode.
- Click ‘Windows keys and R‘ together to open Run box.
- Type msconfig and click OK
- In the System Configuration box, go to the Boot tab and choose Safe Mode and click OK.
To stop the malicious process:
- Click Windows Keys + R key to open Run box.
- Type taskmgr > OK to open task manager.
- Find malicious process, right-click it and click End Process.
To Uninstall .HILDA from Windows:
- For Windows XP/ Windows Vista/ Windows 7 , Open start menu > Control Panel > Doble click Add or Remove programs > Select undesirable software > Remove
- For Windows 8/ Windows 10, Access menu > Control Panel > Unistall a Program > Right click the program > Select Uninstall.
To Uninstall .HILDA file virus from the Control panel:
- Press Windows key + R key to open Run window.
- Input Control Panel in Run window > Enter key.
- Click on Uninstall a program option under the Programs menu.
- Find .HILDA File virus related program and click on the Uninstall button.
To remove .HILDA file virus from browser:
- For Google Chrome, Click Chrome menu > More tools > Click Extensions > Select .HILDA file virus and unwanted extensions > Click trash bin icon.
- For Mozilla Firefox, Navigate to browser menu > Add-ons > Select .HILDA file virus and unwanted extensions or any other malicious add-ons > Disable or Remove button.
- For Internet Explorer, Click Tools > Manager Add-on Tools and Extensions > Select .HILDA file virus and unwanted extensions and add-ons > Click Remove or Disable button.
Try to Recover Encrypted files:
Always use a highly advanced and powerful data recovery suite that can recover all types of lost encrypted or permanently deleted files.
- Download a powerful data recovery software of your choice.
- Run the software and click on the location to scan for missing or deleted files and then click Scan.
- Wait for the scan to complete as it may take time. Obviously, not all Softwares guarantee a 100% recovery of all files but do have some chance to get your data back.
Precautions to counter HILDACRYPT:
- Always choose/ download Custom installations no matter what software you are going to install.
- Check all hidden options which attempts to install additional programs you don’t need.
- Scan all downloads or downloaded attachments of email before you open them.
- Never should a person open any attachment from unknown or spam emails.
- Do not visit adult/ shady websites or torrent sites.
- Not to update any app from an unofficial website. Always prefer originality over copyright.
- Keep a close eye on Windows Firewall security and keep it on.
- Use a powerful anti-virus program and always keep it updated.
- Keep regular backups of your data or important files.
- Create a system restore point for security purposes.
It will be naive to think that hackers will feel obliged to help you restore data when they don’t have to. The more people give hackers the money, the more profitable ransomware becomes. If you end up in a position like this, investing the money into backup would be a better choice than supporting the kind of criminal activity that does billions worth damage. The simple thing you can do when ransomware infects implement an anti-malware program to get rid of the file encoding vulnerability. Further, we should accept the fact that the anti-malware program will only eliminate the infection and not assist in file decrypting.
In short, if your files are encrypted by ransomware, paying the ransom shall be your last option. Follow the above removal methods/ procedures for keeping your data safe before it brings you to a stage where you might face dangerous scenarios. It is more important to get rid of the data encrypting malware and make sure you frequently backup all your important files.

This was all about HILDACRYPT ransomware and it further brings me back to the new attack REDUCTOR. Have you read about it yet? Are you aware enough? It’s Evil, malicious, and dangerous, but more importantly, smart. In the next section, you will get to know better about how the malware threats are increasing and a small section about risk management precautions. The malware was spotted in April this year that allows hackers to manipulate Hypertext Transfer Protocol Secure (HTTPS) traffic by tweaking a browser’s random numbers generator, used to ensure a private connection between the client and server. The malware has been observed to replace legitimate installers with infected ones and further decode encrypted TLS traffic.



