In the 21st century, modern cars are utilizing a lot of innovation and technology to stay updated with the rising demands of customers. As a result, it is constantly connected to the web that makes it incredibly defenseless and simple to hack utilizing different malware techniques and software. Other undetected security defects that is exhibited by these modern vehicles makes it all the more vulnerable to cyber attacks. Connected vehicles are quickly expanding and different gadgets are connected with the car that needs to communicate remotely in order to operate the users from Wi-Fi and utilize other drive assistance. Automotive security field are prone to a number of security threats since modern cars are vulnerable to face a high level of security issues.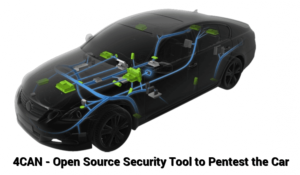
Vehicle-to-Vehicle Communications is built up utilizing Wireless system that permits two vehicles to have proper communication on the street and also permits to diminish the car’s speed if another car comes nearer. In this case, the hacker could be mishandling the defect in the remote correspondence innovation thus diminishing the vehicle’s speed without the driver being aware about it. These modern cars could also be attacked by ruinous malware where the V2V framework turns into a vector, and a malevolent on-screen character makes the malware to infect other connected vehicles.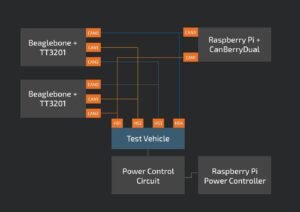
Malware and Exploits
Present day modern car technologies have a designed framework which permits the vehicle to connect the owner’s cell phones to the main framework system. Thus, allowing the car’s owner to attend to telephone calls, SMS, play music or recordings without any kind of interruption. Recent powerful malware attacks target the connected mobile phones in order to gain an easy access to infect these modern vehicles.
Vehicle Theft and Key Fob Hacking
Key fob hacking is a methodology that empowers an attacker to enter the vehicle without getting detected. This framework is commonly utilized by hackers and could be used by anyone with the right kind of techniques and hardware. Usually in such a situation, the attacker blocks the signal from the remote key and locks the vehicle. Furthermore, it also sends signal to the main framework to hack the car. As per McAfee Research, one variation of the assault utilizes a jammer to obstruct the signal. The jammer meddles with the electromagnetic waves used to communicate with the vehicle, thus obstructing the signal and keeping the vehicle from locking, giving access to only the attacker.
Vulnerable Data and Tracking
Connected Cars are remotely controlled by hackers in order to gain access to touchy individual information about the drivers from the outer gadgets, for example, contact details, bank message, calls history and even melodic tastes that associated with the vehicles. This information is illegally acquired by hackers, cybercriminals, and Governments to utilize it for different purposes, for example, spying and following the individuals, promoting or protection contracts.
Counterfeit Car Data
Advanced information can be adjusted and faked. By altering data, for instance, sullying tests or execution, fabricating results to expand deals, etc. Additionally, drivers could change auto experiences, for instance, separate set out to deceive insurance companies or future buyers.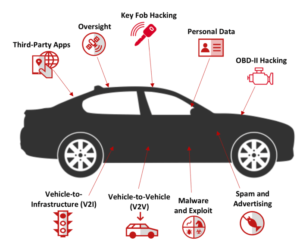
4CAN V2( FIND VULNERABILITIES IN MODERN CARS)
In the most recent times, companies manufacture modern vehicles that are associated with certain administrative portals with limited security. We often come across motion pictures where we find modern cars getting hacked remotely look very far-fetched. Unfortunately, in the contemporary world, this has turned into a reality. Cisco designed an open-source device called 4CAN to help test for vulnerabilities in modern cars. Vulnerabilities in the framework of these vehicles can be a source of genuine danger for the driver as well as the passenger. This newly equipped security instrument 4CAN lets the security specialists play out an assortment of security appraisals in parts associated with the vehicle in order to ensure that everything is working fine. The specialists check the Wifi, Bluetooth, and cell correspondence convention, Controller Area Network (CAN) also called CAN bus.”
In the event, that the hackers physically gain access to the CAN bus by means of an ODB2 connector that is fixed on the driver’s-side lower dash. It can be effectively assumed that the hackers can now easily gain total control over the car. CAN bus communicate with different basic segments including airbags and brakes and other non-basic segments, for example, radio or interior lights. By getting to the CAN bus, analyzers and technical analysts can test the different parts to discover any vulnerabilities.
George Tarnovsky, an individual from Cisco’s Customer Experience Assessment and Penetration Team (CX APT) designed the 4CAN with the main point of view being to investigate the vulnerabilities in modern cars through the following objectives –
- Approving a detailed and systemic communicative approach for intra-CAN bus communication.
- Fluffing (sending randomized payloads) to different parts of a vehicle to recognize vulnerabilities.
- Investigating the CAN directives used to control/communicate with the vehicle.
- Rearrange our testbench set up to keep everything composed and in a state of harmony.
Before 4CAN arrived, there were three CAN gadgets designed to simultaneously test four CAN buses. Alongside two TT3201, there were three-channel CAN Capes connected to Beaglebones, and one CanBerra Dual joined to a Raspberry Pi. Likewise another Raspberry Pi was introduced to remotely control the test vehicle. With this arrangement, they could test sending CAN outlines between any two mixes of CAN channels however the testing procedure was troublesome and time consuming as it required to setting up a great deal of wires to set up the whole association.
As per Cisco, by using 4CAN, the testbench arrangement is immeasurably rearranged. With a solitary Raspberry Pi, we can at the same time test four CAN channel, and since the 4CAN uncovered the whole 40-stick GPIO header, one can even remotely control the test vehicle.4CAN enabled the analysts to test the vulnerabilities including sniff CAN traffic, send CAN messages, replay caught CAN traffic, actualize a CAN portal to encourage CAN-in-the-center and different tests.



